Throughout this guide, we break down the deployment and configuration of the FedRAMP policy with the following sections:
Introduction
FedRAMP (Federal Risk and Authorization Management Program) is a standardized approach for assessing, authorizing, and monitoring cloud service providers (CSPs) that provide service to federal agencies. Through a rigorous and comprehensive process, FedRAMP ensures that CSPs meet security standards by providing a baseline set of security controls in order to enhance the overall security for federal information systems.
Anchore’s FedRAMP policy validates whether container images scanned by Anchore Enterprise are compliant with the FedRAMP Vulnerability Scanning Requirements and also validates them against FedRAMP controls specified in NIST 800-53 Rev 5 and NIST 800-190.
Anchore’s FedRAMP policy only checks for specification requirements relevant to software supply chain security.
Anchore’s FedRAMP policy checks for the following specifications:
- AC-6(10) ACCESS CONTROL: Prevent Non-Privileged Users from Executing Privileged Functions
- CM-2(2), CM-3(1), CM-6 CONFIGURATION MANAGEMENT: Baseline Configuration | Configure Systems and Components for High-risk Areas
- CM-10 CONFIGURATION MANAGEMENT: Software Usage Restrictions
- CM-5(5) CONFIGURATION MANAGEMENT: Access Restrictions for Change | Privilege Limitation for Production and Operation
- CM-7(1) CONFIGURATION MANAGEMENT: Least Functionality - Network Port Exposure Checks
- CM-7(5), CM-8(3) CONFIGURATION MANAGEMENT: Least Functionality - Container Image Build Content Checks
- IA-05(7) IDENTIFICATION AND AUTHENTICATION: Authenticator Management | No Embedded Unencrypted Static Authenticators
- RA-5, SI-02(2) RISK ASSESSMENT: Vulnerability Monitoring and Scanning
- SC-5 SYSTEM AND COMMUNICATIONS PROTECTION: Denial-of-Service Protection
Enabling the FedRAMP Policy
If you are an Anchore Enterprise customer, you will receive an email, which includes a json file for the specific FedRAMP policy that comes with your service.
Navigate to the Policies tab in Anchore Enterprise and click on the ‘Import Policy’.
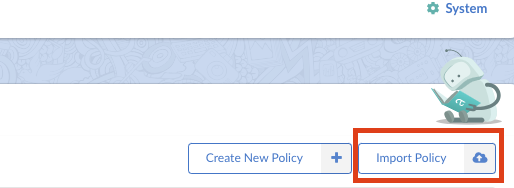
Drag and drop, or paste the .json file to import the policy into Anchore Enterprise.
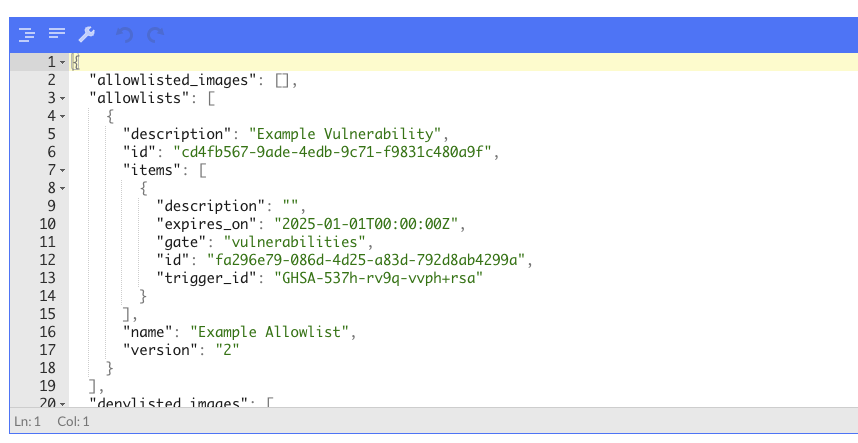
Or run the following command using AnchoreCTL
# anchorectl policy add --input FedRAMP_policy_pack_json_file ✔ Added policy Name: Anchore FedRAMP v5 Checks Policy Id: 1346c770-c49b-46be-b8f0-961ee40afbc3 Active: false Updated: 2024-05-01T21:09:41ZAfter a successful import, the FedRAMP policy will be available in the Policies tab.
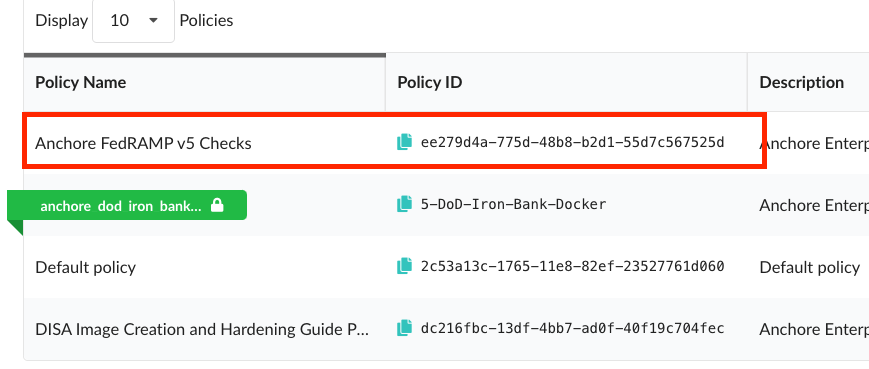
Or run the following command using AnchoreCTL
# anchorectl policy list ✔ Fetched policies ┌───────────────────────────┬──────────────────────────────────────┬────────┬──────────────────────┐ │ NAME │ POLICY ID │ ACTIVE │ UPDATED │ ├───────────────────────────┼──────────────────────────────────────┼────────┼──────────────────────┤ │ Default policy │ 2c53a13c-1765-11e8-82ef-23527761d060 │ true │ 2024-04-25T18:21:54Z │ │ Anchore FedRAMP v5 Checks │ 1346c770-c49b-46be-b8f0-961ee40afbc3 │ false │ 2024-04-25T18:23:10Z │ └───────────────────────────┴──────────────────────────────────────┴────────┴──────────────────────┘In order to activate the FedRAMP policy, simply click on the circle under ‘Active’.
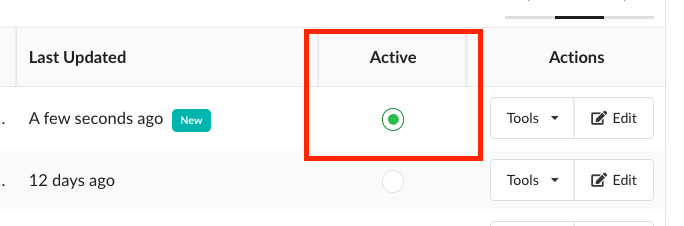
Once activated, you will see that the FedRAMP policy is highlighted in green.
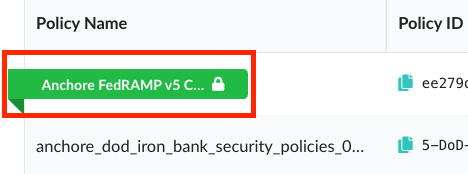
Or run the following command using AnchoreCTL
# anchorectl policy activate 1346c770-c49b-46be-b8f0-961ee40afbc3 ✔ Activate policy Name: Anchore FedRAMP v5 Checks Policy Id: 1346c770-c49b-46be-b8f0-961ee40afbc3 Active: true Updated: 2024-04-25T18:30:24ZNavigate to the Image tab in Anchore Enterprise and you will now be able to evaluate an image with the FedRAMP policy.
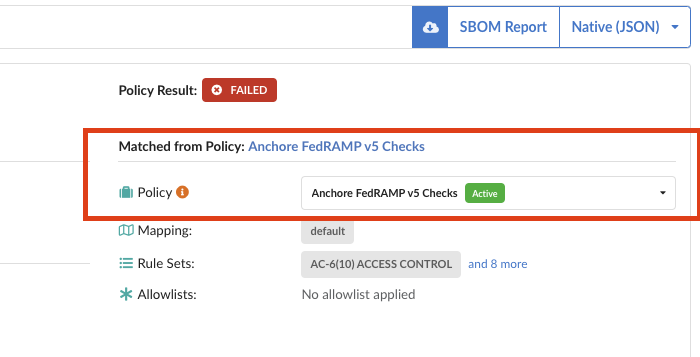
Or run the following command using AnchoreCTL
As an example, we will add a centos image and evaluate it using the FedRAMP policy. please give it some time for Anchore to analyze the image when added
# anchorectl image add docker.io/centos:latest --wait ✔ Added Image docker.io/centos:latest ✔ Analyzed Image docker.io/centos:latest Image: status: analyzed (active) tag: docker.io/centos:latest digest: sha256:a1801b843b1bfaf77c501e7a6d3f709401a1e0c83863037fa3aab063a7fdb9dc id: 5d0da3dc976460b72c77d94c8a1ad043720b0416bfc16c52c45d4847e53fadb6 distro: centos@8 (amd64) layers: 1To apply the active FedRAMP policy and see all the details of violation:
#anchorectl image check docker.io/centos:latest --detailTo apply the active FedRAMP policy and get a simple pass/fail check:
#anchorectl image check -f docker.io/centos:latest ✔ Evaluated against policy [failed] docker.io/centos:latest Tag: docker.io/centos:latest Digest: sha256:a1801b843b1bfaf77c501e7a6d3f709401a1e0c83863037fa3aab063a7fdb9dc Policy ID: 1346c770-c49b-46be-b8f0-961ee40afbc3 Last Evaluation: 2024-04-25T18:40:15Z Evaluation: fail Final Action: stop Reason: policy_evaluation error: 1 error occurred: * failed policies:
Configuring Rule Sets for the FedRAMP Policy
Some of the control specifications need configuration based on the user’s environment. The control specifications are represented by ‘Rule Sets’ in Anchore Enterprise. Navigate to the Policies tab and click on the ‘Edit’ under ‘Actions’.
It is recommended all configuration changes to rule sets be done in the Anchore Enterprise UI.
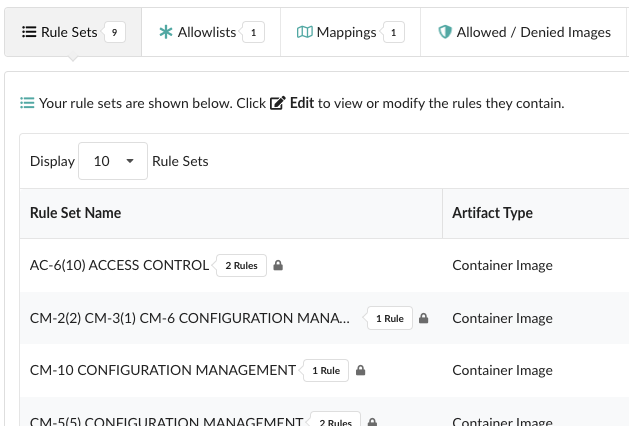
You will be able to view all the FedRAMP specifications Anchore analyzes for. Under each Rule Set, please edit the ones that require configuration.
As an example, a user may need to change the port configuration for CM-7(1) CONFIGURATION MANAGEMENT, which checks for network port exposures.
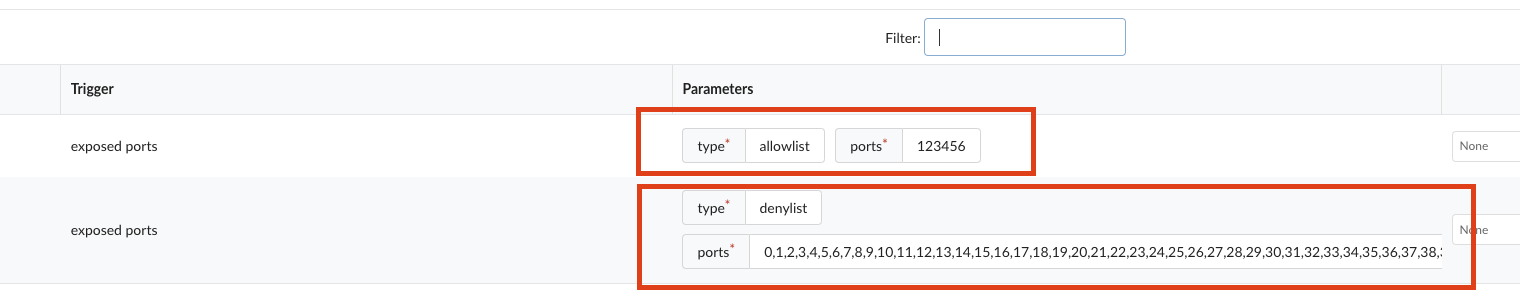
Make sure to go through each of the Rule Sets to configure all applicable specifications. Save and close.
The following rule sets MUST be configured before using the FedRAMP policy:
- CM-2(2), CM-3(1), CM-6 CONFIGURATION MANAGEMENT: Baseline Configuration | Configure Systems and Components for High-risk Areas
- CM-10 CONFIGURATION MANAGEMENT: Software Usage Restrictions
- CM-5(5) CONFIGURATION MANAGEMENT: Access Restrictions for Change | Privilege Limitation for Production and Operation
- CM-7(1) CONFIGURATION MANAGEMENT: Least Functionality - Network Port Exposure Checks
- CM-7(5), CM-8(3) CONFIGURATION MANAGEMENT: Least Functionality - Container Image Build Content Checks