Policy Overview
What is a policy?
A policy is composed of a set of rules that are used to perform an evaluation on a source repository or container image. These rules include—but are not limited to—checks on security, known vulnerabilities, configuration file contents, the presence of credentials, manifest changes, exposed ports, or any user defined checks.
Policies can be deployed site wide, or customized to run against specific sources, container images, or categories of application. For additional information, refer to the Policy concepts section.
Once a policy has been applied to a source repository or image container, it can return one of two results:
“Passed” indicating that source or image complies with your policy.
“Failed” indicating that the source or image is non-compliant with your policy.
A policy includes the following elements:
Rule Sets
A policy is made up from a set of rules that are used to perform an evaluation on a source repository or container image. These policies can be deployed site wide or customized for specific source repositories, container images, or categories of applications. A policy may contain one or more named rule sets.
Policy rule checks are made up of gates and triggers. A gate is a set of policy checks against broad categories like vulnerabilities, secret scans, licenses, and so forth. It will include one or more triggers, which are checks specific to the gate category. For additional information, refer to the Policy Rules concepts section.
The policy additionally specifies the following action results:
- STOP: Critical error that should stop the deployment by failing the policy evaluation.
- WARN: Issue a warning.
- GO: Okay to proceed.
The result of an evaluation will be based on the actions configured in your rule set.
If you are creating a policy rule for a source repository, only vulnerabilities checks are available.
Allowlists
An allowlist contains one or more exceptions that can be used during policy evaluations, such as allowing a CVE to be excluded. A policy may contain multiple allowlists.
Mappings
A policy mapping defines which policies and allowlists should be used to perform the policy evaluation of a given source repository or container image. A policy may contain multiple mappings including wildcard mappings that apply to multiple elements.
Allowed Images
An allowed images list defines one or more images that will always pass policy evaluation regardless of any policy violations. Allowed images can be specified by name, image ID, or image digest. A policy contains a single list of allowed images.
Denied Images
A denied images list defines one or more images that will always fail policy evaluation. Denied images can be specified by name, image ID, or image digest. A policy contains a single list of denied images.
Listing Policies
The Policies tab contains a table that lists the policies defined within an account.
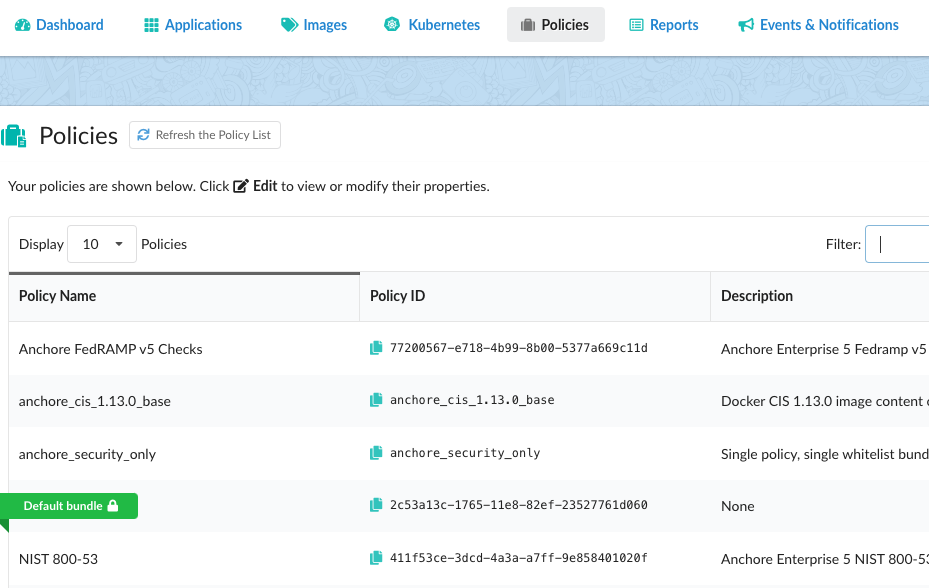
Note: A lock icon next to the policy name indicates that the policy cannot be deleted. Policy rules that are used by policy mappings in the policy (which will be listed under the Mappings column entry within the Edit option) cannot be deleted until they are removed from every associated mapping.
Policies can also be managed directly using the REST API or the anchorectl policy command. It is recommended that any policy configuration be handled via UI and not AnchoreCTL
# anchorectl policy list
✔ Fetched policies
┌────────────────┬──────────────────────────────────────┬────────┬──────────────────────┐
│ NAME │ POLICY ID │ ACTIVE │ UPDATED │
├────────────────┼──────────────────────────────────────┼────────┼──────────────────────┤
│ Default policy │ 2c53a13c-1765-11e8-82ef-23527761d060 │ true │ 2023-10-25T20:39:28Z │
│ devteam1policy │ da8208a2-c8ae-4cf2-a25b-a52b0cdcd789 │ false │ 2023-10-25T20:47:16Z │
└────────────────┴──────────────────────────────────────┴────────┴──────────────────────┘
** times are reported in UTC
Using the policy get command, summary or detailed information about a policy can be retrieved. The policy is referenced using its unique POLICY ID.
# anchorectl policy get 2c53a13c-1765-11e8-82ef-23527761d060
✔ Fetched policy
Name: Default policy
ID: 2c53a13c-1765-11e8-82ef-23527761d060
Comment: Default policy
Policies:
- artifactType: image
comment: System default policy
id: 48e6f7d6-1765-11e8-b5f9-8b6f228548b6
name: DefaultPolicy
rules:
- action: STOP
gate: dockerfile
id: ce7b8000-829b-4c27-8122-69cd59018400
params:
- name: ports
value: "22"
- name: type
value: denylist
trigger: exposed_ports
...
...
The policy can be downloaded in JSON format by passing the --detail parameter.
# anchorectl policy get 2c53a13c-1765-11e8-82ef-23527761d060 --detail -o json-raw > policy.json
✔ Fetched policy
Tools and Edit
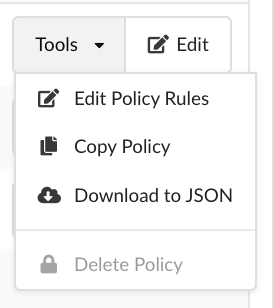
The Tools dropdown menu in the Actions column provides options to:
- Edit the policy
- Copy the policy
- Download the policy as a JSON document
- Delete the policy (if it is not being used by any policy mapping)
The Edit button provides options to view and edit:
- Rule Sets
- Allowlists
- Mappings
- Allowed/Denied Images