Introduction
The Evaluation Preview feature allows you to perform a test evaluation on an image to verify the mapping, policies and allowlists used to evaluate an image.
To test an image you should enter the name of the image, optionally including the registry if the image is not stored on docker.io In the example below an evaluate was requested for library/debian:latest because no registry was specified the default, docker.io registry was used.
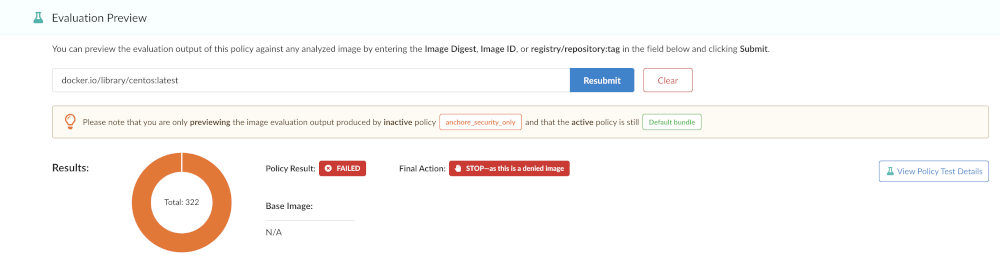
Here we can see that the image was evaluated against the policy named “anchore_security_only” and failed, resulting in a STOP action.
Clicking the “View Policy Test Details” will show a more detailed report.
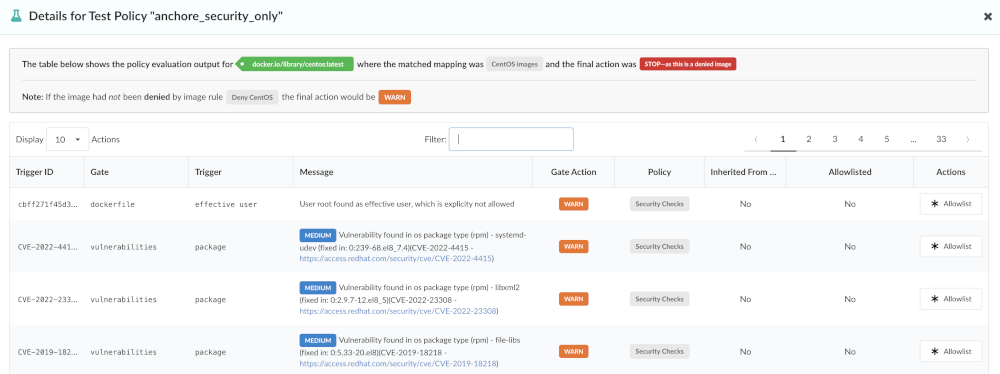
The image was evaluated using the mapping named  and the evaluation failed as the image was found in a denylist.
and the evaluation failed as the image was found in a denylist. 
The next line explains that the image had been denylisted by the Deny CentOS denylist rule, however if the image was not denylisted, it would only have produced a WARN instead of a failure.

The subsequent table lists the policy checks that resulted in any Warn or Stop (failure) checks.
The policy checks are performed on images already analyzed and recorded in Anchore Enterprise. If an image has been added to the system but has not yet completed analysis, then the system will display the following error:
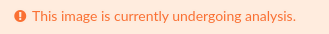
If the evaluation test is re-run after a few minutes, the image will likely have completed analysis and a policy evaluation result will be returned.
If the image specified has not been analyzed by the system and has not been submitted for analysis, then the following error message will be displayed.

Policies with AnchoreCTL
The anchorectl image check command can be used to evaluate a given image for policy compliance via the CLI rather than the UI. This will allow for the testing of images against policies in your pipeline and action to be taken depending on the result of the evaluation.
The image to be evaluated can be in the following format:
Image Digest Image ID registry/repo:tag
Below is an example of how you would use the command with an image in the registry/repo:tag format;
anchorectl image check docker.io/debian:latest
✔ Evaluated against policy [failed] docker.io/debian:latest
Tag: docker.io/debian:latest
Digest: sha256:0fcb5a38077422c4e70c5c43be21831193ff4559d143e27d8d5721e7a814bdcc
Policy ID: 2c53a13c-1765-11e8-82ef-23527761d060
Last Evaluation: 2023-10-25T20:34:43Z
Evaluation: fail
By default, only the summary of the evaluation is shown. Passing the --detail parameter will show the policy checks that raised warnings or errors.
anchorectl image check docker.io/debian:latest --detail
✔ Evaluated against policy [failed] docker.io/debian:latest
Tag: docker.io/debian:latest
Digest: sha256:0fcb5a38077422c4e70c5c43be21831193ff4559d143e27d8d5721e7a814bdcc
Policy ID: 2c53a13c-1765-11e8-82ef-23527761d060
Last Evaluation: 2023-10-25T20:35:05Z
Evaluation: fail
Final Action: stop
Reason: policy_evaluation
Policy Evaluation Details:
┌─────────────────┬─────────────┬────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────┬────────┐
│ GATE │ TRIGGER │ DESCRIPTION │ STATUS │
├─────────────────┼─────────────┼────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────┼────────┤
│ dockerfile │ instruction │ Dockerfile directive 'HEALTHCHECK' not found, matching condition 'not_exists' check │ warn │
│ vulnerabilities │ package │ MEDIUM Vulnerability found in os package type (dpkg) - libgnutls30 (CVE-2011-3389 - https://security-tracker.debian.org/tracker/CVE-2011-3389) │ warn │
│ vulnerabilities │ package │ CRITICAL Vulnerability found in os package type (dpkg) - zlib1g (CVE-2022-37434 - https://security-tracker.debian.org/tracker/CVE-2022-37434) │ stop │
└─────────────────┴─────────────┴────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────┴────────┘
In this example we specified library/repo:tag which could be ambiguous. At the time of writing the image Digest for library/debian:latest was sha256:0fc..... however previously different images may have been tagged as library/debian:latest. The --history parameter can be passed to show historic evaluations based on previous images or previous policies.
Anchore supports allowlisting and denylisting images by their name, ID or digest. A denylist or allowlist takes precedence over any policy checks. For example if an image is explicitly listed as denylisted then even if all the individual policy checks pass the image will still fail evaluation. If you are unsure whether the image is hitting an allowlist/denylist, this information can be seen via the reason when you pass the --detail parameter.
anchorectl image check docker.io/debian:latest --detail
✔ Evaluated against policy [failed] docker.io/debian:latest
Tag: docker.io/debian:latest
Digest: sha256:0fcb5a38077422c4e70c5c43be21831193ff4559d143e27d8d5721e7a814bdcc
Policy ID: 2c53a13c-1765-11e8-82ef-23527761d060
Last Evaluation: 2023-10-25T20:39:36Z
Evaluation: fail
Final Action: stop
Reason: denylisted
Policy Evaluation Details:
┌─────────────────┬─────────────┬────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────┬────────┐
│ GATE │ TRIGGER │ DESCRIPTION │ STATUS │
├─────────────────┼─────────────┼────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────┼────────┤
│ dockerfile │ instruction │ Dockerfile directive 'HEALTHCHECK' not found, matching condition 'not_exists' check │ warn │
│ vulnerabilities │ package │ MEDIUM Vulnerability found in os package type (dpkg) - libgnutls30 (CVE-2011-3389 - https://security-tracker.debian.org/tracker/CVE-2011-3389) │ warn │
└─────────────────┴─────────────┴────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────┴────────┘
In this example even though the image only had one policy check that raised a warning, the reason value shows that the image fails policy evaluation since it is present on a denylist.
Evaluating status based on Digest or ID
Evaluating an image specified by name as shown above is not recommended since an image name is ambiguous. For example the tag docker.io/library/centos:latest refers to whatever image has the tag library/centos:latest at the time of evaluation. At any point in time another image may be tagged as library/centos:latest.
It is recommended that images are referenced by their digest. For example at the time of writing the digest of the ‘current’ library/centos:latest image is sha256:191c883e479a7da2362b2d54c0840b2e8981e5ab62e11ab925abf8808d3d5d44
If the image to be evaluated is specified by Image ID or Image Digest then the --tag parameter must be added. Policies are mapped to images based on registry/repo:tag so since an Image ID may may to multiple different names we must specify the name user in the evaluation.
For example - referencing by Image Digest:
anchorectl image check docker.io/debian@sha256:0fcb5a38077422c4e70c5c43be21831193ff4559d143e27d8d5721e7a814bdcc --detail --tag docker.io/debian:latest
✔ Evaluated against policy [failed] docker.io/debian@sha256:0fcb5a38077422c4e70c5c43be21831193ff4559d143e27d8d5721e7a814bdcc
Tag: docker.io/debian:latest
Digest: sha256:0fcb5a38077422c4e70c5c43be21831193ff4559d143e27d8d5721e7a814bdcc
Policy ID: 2c53a13c-1765-11e8-82ef-23527761d060
Last Evaluation: 2023-10-25T20:44:24Z
Evaluation: fail
Final Action: stop
Reason: denylisted
Policy Evaluation Details:
┌─────────────────┬─────────────┬────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────┬────────┐
│ GATE │ TRIGGER │ DESCRIPTION │ STATUS │
├─────────────────┼─────────────┼────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────┼────────┤
│ dockerfile │ instruction │ Dockerfile directive 'HEALTHCHECK' not found, matching condition 'not_exists' check │ warn │
│ vulnerabilities │ package │ MEDIUM Vulnerability found in os package type (dpkg) - libgnutls30 (CVE-2011-3389 - https://security-tracker.debian.org/tracker/CVE-2011-3389) │ warn │
│ vulnerabilities │ package │ CRITICAL Vulnerability found in os package type (dpkg) - zlib1g (CVE-2022-37434 - https://security-tracker.debian.org/tracker/CVE-2022-37434) │ stop │
└─────────────────┴─────────────┴────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────┴────────┘
For example - referencing by image ID:
anchorectl image check dd8bae8d259fed93eb54b3bca0adeb647fc07f6ef16745c8ed4144ada4d51a95 --detail --tag docker.io/debian:latest
✔ Evaluated against policy [failed] dd8bae8d259fed93eb54b3bca0adeb647fc07f6ef16745c8ed4144ada4d51a95
Tag: docker.io/debian:latest
Digest: sha256:0fcb5a38077422c4e70c5c43be21831193ff4559d143e27d8d5721e7a814bdcc
Policy ID: 2c53a13c-1765-11e8-82ef-23527761d060
Last Evaluation: 2023-10-25T20:45:20Z
Evaluation: fail
Final Action: stop
Reason: denylisted
Policy Evaluation Details:
┌─────────────────┬─────────────┬────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────┬────────┐
│ GATE │ TRIGGER │ DESCRIPTION │ STATUS │
├─────────────────┼─────────────┼────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────┼────────┤
│ dockerfile │ instruction │ Dockerfile directive 'HEALTHCHECK' not found, matching condition 'not_exists' check │ warn │
│ vulnerabilities │ package │ MEDIUM Vulnerability found in os package type (dpkg) - libgnutls30 (CVE-2011-3389 - https://security-tracker.debian.org/tracker/CVE-2011-3389) │ warn │
│ vulnerabilities │ package │ CRITICAL Vulnerability found in os package type (dpkg) - zlib1g (CVE-2022-37434 - https://security-tracker.debian.org/tracker/CVE-2022-37434) │ stop │
└─────────────────┴─────────────┴────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────┴────────┘
If you want to specify a policy to use for the evaluation other than the policy that is currently set as the default policy, you can use the parameter -p or --policy and then specify the policy ID.
anchorectl image check sha256:a1801b843b1bfaf77c501e7a6d3f709401a1e0c83863037fa3aab063a7fdb9dc --detail --tag docker.io/centos:latest --policy 6d260d49-45e3-4dcd-bfd8-cc8f00e10501
✔ Evaluated against policy [passed] sha256:a1801b843b1bfaf77c501e7a6d3f709401a1e0c83863037fa3aab063a7fdb9dc
Tag: docker.io/centos:latest
Digest: sha256:a1801b843b1bfaf77c501e7a6d3f709401a1e0c83863037fa3aab063a7fdb9dc
Policy ID: 6d260d49-45e3-4dcd-bfd8-cc8f00e10501
Last Evaluation: 2024-12-23T12:48:24Z
Evaluation: pass
Final Action: go
Reason: allowlisted
Policy Evaluation Details:
┌──────┬─────────┬─────────────┬────────┬────────────────┐
│ GATE │ TRIGGER │ DESCRIPTION │ ACTION │ RECOMMENDATION │
├──────┼─────────┼─────────────┼────────┼────────────────┤
└──────┴─────────┴─────────────┴────────┴────────────────┘
In this example, you will see I specified a new policy at the end of the command using --policy. In this policy, I had added the image being evaluated to an allowlist, and you can see that the Evaluation, Final Action, and Reason have all changed to show the outcome of testing the image against this new policy.
The final feature to show a brief example of here is valuable for use in your pipeline and it is the -f or --fail-based-on-results parameter. When your image successfully passes evaluation, you will not see anything different when using this flag. However, when the image fails the the evaluation test, it causes the command itself to fail as if an error has been hit. This sets the command return code to 1 which can be used in your pipeline to differentiate between an image that passes and an image that fails and allows you to decide on the next action depending on this result.
anchorectl image check sha256:a1801b843b1bfaf77c501e7a6d3f709401a1e0c83863037fa3aab063a7fdb9dc --detail --tag docker.io/centos:latest --fail-based-on-results
✔ Evaluated against policy [failed] sha256:a1801b843b1bfaf77c501e7a6d3f709401a1e0c83863037fa3aab063a7fdb9dc
Tag: docker.io/centos:latest
Digest: sha256:a1801b843b1bfaf77c501e7a6d3f709401a1e0c83863037fa3aab063a7fdb9dc
Policy ID: anchore_secure_default
Last Evaluation: 2024-12-23T12:20:56Z
Evaluation: fail
Final Action: stop
Reason: denylisted
Policy Evaluation Details:
┌─────────────────┬─────────────────┬─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────┬────────┬───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────┐
│ GATE │ TRIGGER │ DESCRIPTION
│ ACTION │ RECOMMENDATION
│
├─────────────────┼─────────────────┼─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────┼────────┼───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────┤
│ vulnerabilities │ stale_feed_data │ The vulnerability feed for this image distro is older than MAXAGE (2) days
│ warn │ Please check the feed service logs. It appears the data has no been updated in the last 2 days which could suggest a problem. Details on Anchore Enterprise's feed service can be found in the documentation │
│ │ │
│ │ https://docs.anchore.com/current/docs/configuration/feeds/
│
│ │ │
│ │ If you are unable to resolve this issue via the documentation please contact Anchore support.
│
│ vulnerabilities │ package │ MEDIUM Vulnerability found in os package type (rpm) - vim-minimal-2:8.0.1763-15.el8 (fixed in: 2:8.0.1763-16.el8_5.4)(CVE-2021-4193 - https://access.redhat.com/security/cve/CVE-2021-4193) │ warn │ Packages with low, medium, and high vulnerabilities present can be upgraded to resolve these findings. If upgrading is not possible the finding should be added to an allowlist. │
│ vulnerabilities │ package │ MEDIUM Vulnerability found in os package type (rpm) - libdnf-0.55.0-7.el8 (fixed in: 0:0.63.0-3.el8)(CVE-2021-3445 - https://access.redhat.com/security/cve/CVE-2021-3445) │ warn │ Packages with low, medium, and high vulnerabilities present can be upgraded to resolve these findings. If upgrading is not possible the finding should be added to an allowlist. │
...
error: 1 error occurred:
* failed policies: anchore_secure_default
In the example above, I have omitted some of the results in the table detailing the policies that the image failed on for ease of reading, but we can see in the evaluation status that this image is now failing evaluation again - however, now at the bottom of the output you can see a message error: 1 error occurred: * failed policies: anchore_secure_default this is flag recognising that the image has failed its evaluation and now is forcing the terminal process to return this error(therefore setting the return code to 1) and also providing the name of the policy being used that the image has failed against, which we can see in this example that the policy is just called anchore_secure_default.