Configuring SAML SSO for Anchore with KeyCloak
The JBoss KeyCloak system is a widely used and open-source identity management system that supports integration with applications via SAML and OpenID Connect. It also can operate as an identity broker between other providers such as LDAP or other SAML providers and applications that support SAML or OpenID Connect.
The following is an example of how to configure a new client entry in KeyCloak and configure Anchore to use it to permit UI login by KeyCloak users that are granted access via KeyCloak configuration.
Configuring KeyCloak
Anchore supports multiple IDP configurations, each given a name. For this example we’ll choose the name “keycloak” for our configuration. This is important as that name is used in several URL paths to ensure that the correct configuration is used for validating responses, so make sure you pick a name that is meaningful to your users (they will see it in the login screen) and also that is url friendly.
Some config choices and assumptions specifically for this example:
- Let’s assume that you are running Anchore Enterprise locally. Anchore Enterprise UI is available at:
https://localhost:3000. Replace with the appropriate url as needed. - We’re going to choose
keycloakas the name of this saml/sso configuration within Anchore. This will identify the specific configuration and is used in urls. - Based on that, the Single-SignOn URL for this deployment will be:
https://localhost:3000/service/sso/auth/keycloak - Our SP Entity ID will use the same url:
http://localhost:3000/service/sso/auth/keycloak
Add a Client entry in KeyCloak
See SAML Clients in KeyCloak documentation
For this example, set the following values in “Add Client” screen (these are specific to the settings in this example described above):
- Client ID -
http://localhost:3000/service/sso/auth/keycloak- This will be the SP Entity ID used in the Anchore configuration later - Client Protocol: “saml”
- Client SAML Endpoint: “http://localhost:3000/service/sso/auth/keycloak”
- Client ID -
In the next screen, Client Settings
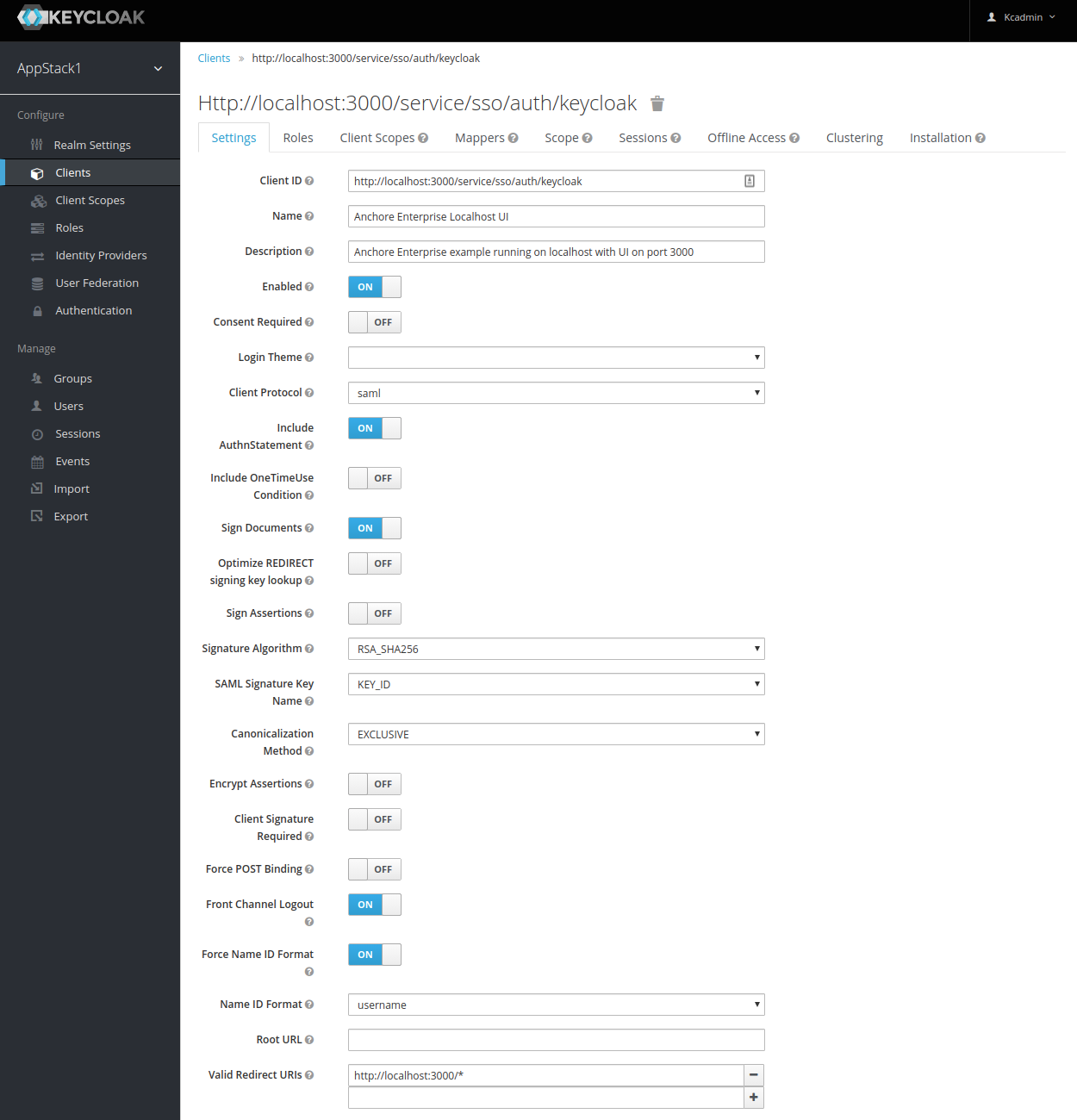
Name - “Anchore Enterprise”. This is only used to display a friendly name to Keycloak users in the KeyCloak UI. Can use any name you like.
Enabled - Select on
Include Authn Statement - Select on
Sign Documents - Select on
Client Sign Authn Requests - Select Off
Sign Assertions - Select off
Encrypt Assertions - Select off
Client Signature Required - Select off
Force Post Binding - Select off. Anchore requires the HTTP Redirect Binding to work, so this setting must be off to enable that.
Force Name ID Format - Select on
Name ID Format - Select username or email (transient uses a generated UUID per login and persistent use the Keycloak user’s UUID)
Root URL - Leave empty
Valid Redirect URIs - Add
http://localhost:3000/service/sso/auth/keycloakBase URL - Leave empty
Master SAML Processing URL -
http://localhost:3000/service/sso/auth/keycloakFine Grain SAML Endpoint Configuration
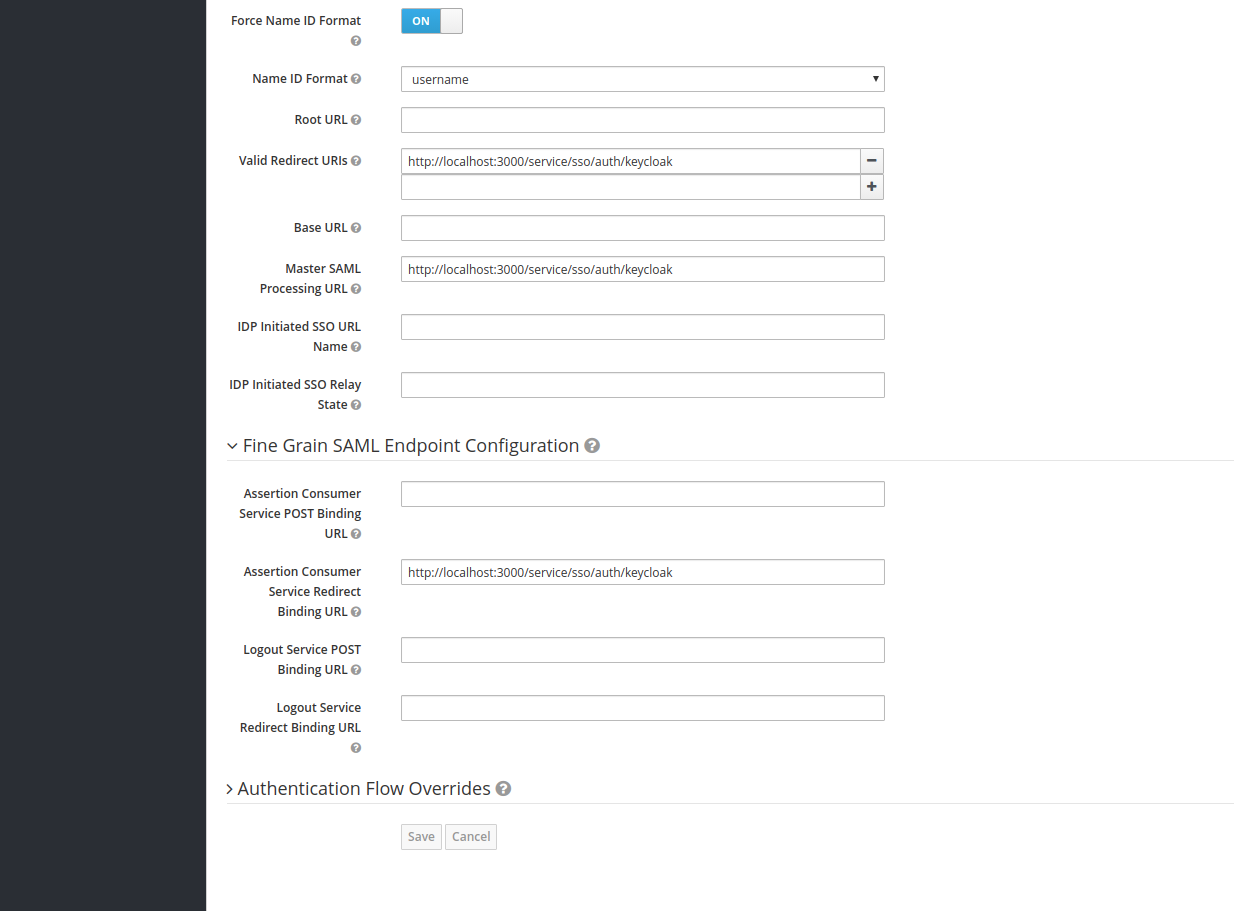
- Assertion Consumer Service Redirect Binding URL -
http://localhost:3000/service/sso/auth/keycloak
- Assertion Consumer Service Redirect Binding URL -
Save the configuration
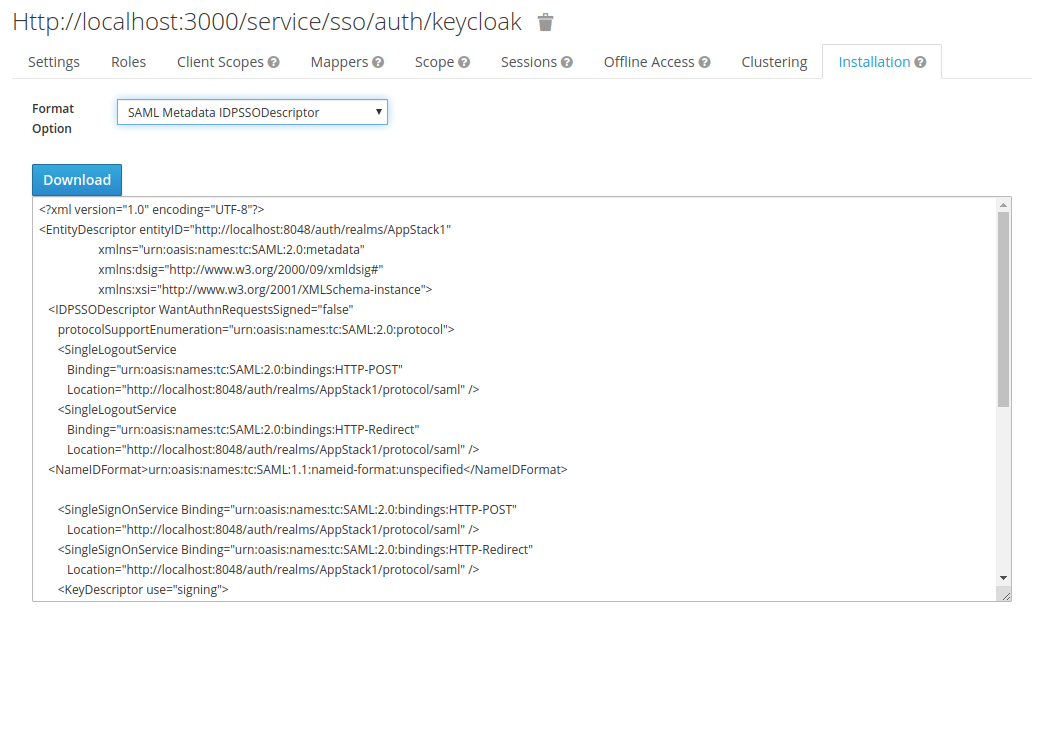
Download the metadata xml to import into Anchore
- Select ‘Installation’ tab.
- Select Format
- Keycloak <= 5.0.0
- Select Format Option - SAML Metadata IDPSSODescriptor
- Keycloak 6.0.0+
- Select Format Option - Mod Auth Mellon files
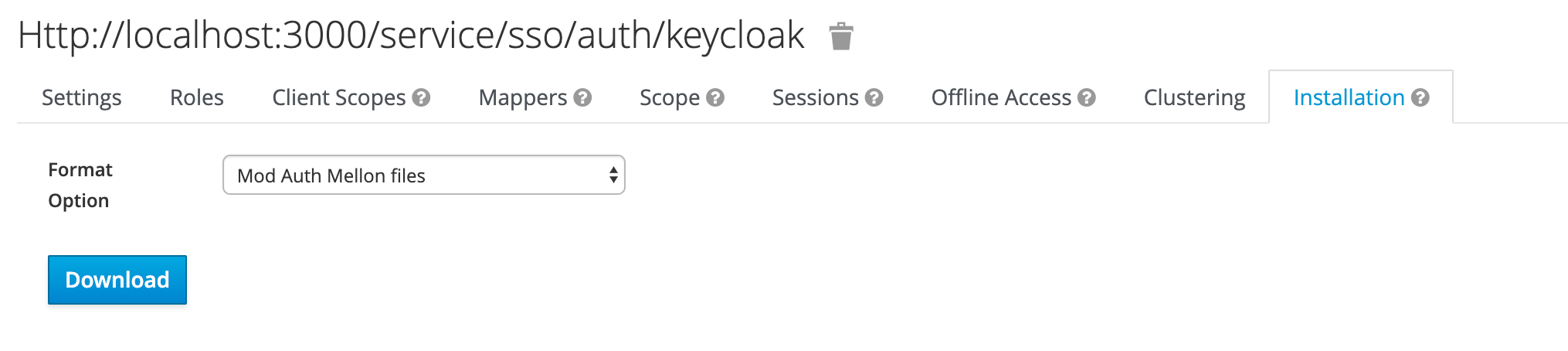
- Unzip the downloaded .zip and locate
idp-metadata.xml
- Download or copy the XML to save in the Anchore configuration
Partial Scoping for the Anchore Enterprise Client in Keycloak
By default, the effective scopes include all roles declared in the Keycloak realm. Anchore Enterprise expects to be able to map roles from Keycloak to roles within Anchore, so limiting it to partial scope instead of full scope prevents sending extra roles to Anchore that cannot be correctly interpreted. To change this default behavior, toggle Full Scope Allowed to OFF and declare the specific roles you want in each client under the Clients –> Anchore Enterprise Client Details –> Dedicated Scopes, Scope tab.
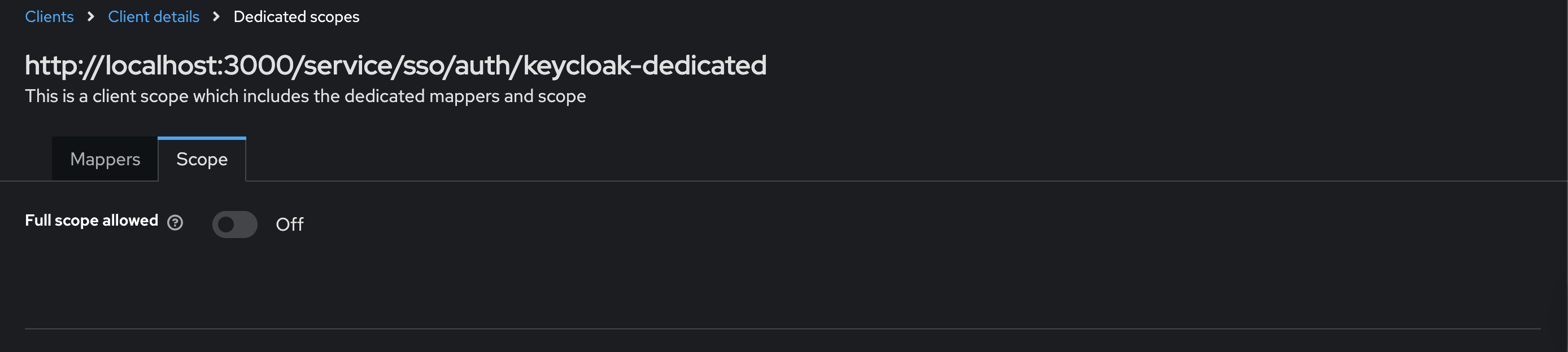
Configure Anchore Enterprise to use the KeyCloak
You’ll need the following information from keycloak in order to configure the SAML record within Anchore:
The name to use fo the configuration, in this example
keycloakMetadata XML downloaded or copied from the previous section
In the Anchore UI, create an SSO IDP Configuration:
Login as admin
Select “Configuration” Tab on the top
Select “SSO” on the left-side menu
Click “Let’s Add One” in the configuration listing
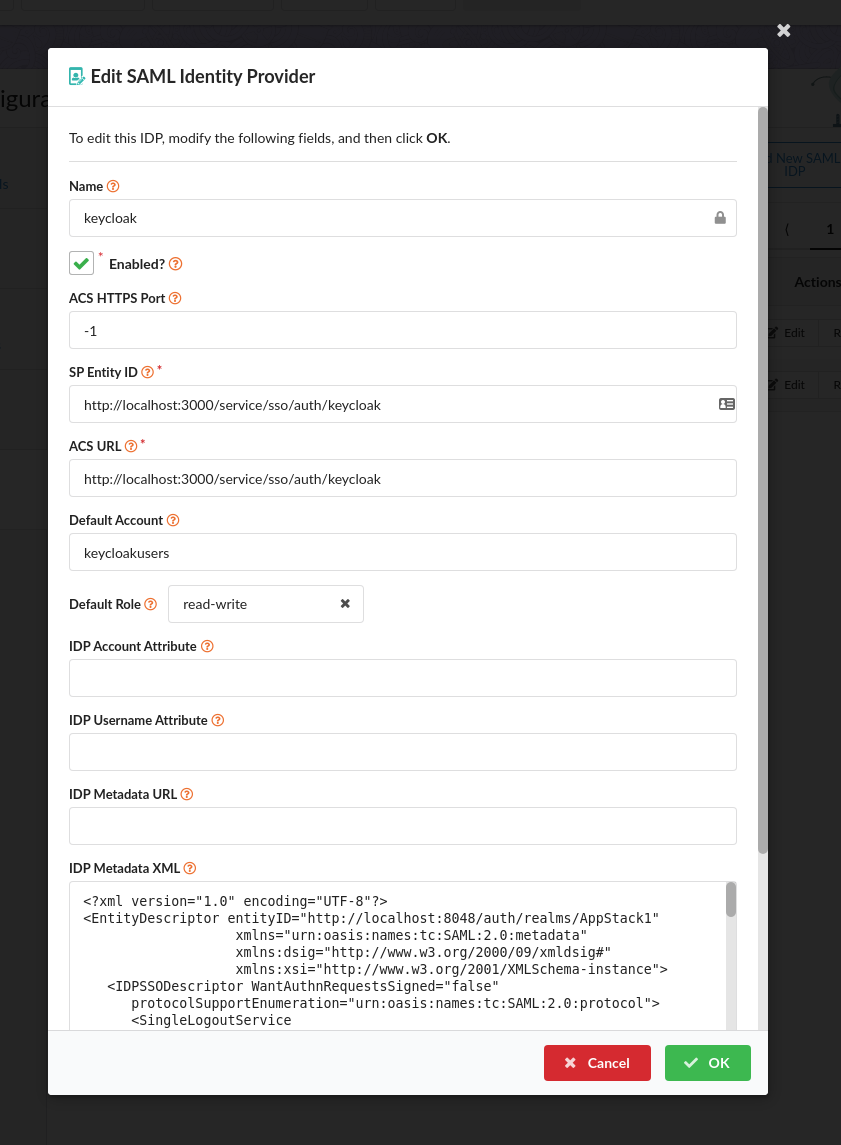
- Enter the values:
- Name: “keycloak” - This is the name of the configuration and will be referenced in login and sso URLs, so we use the value chosen at the beginning of this example
- Enabled: True - This controls whether or not users will be able to login with this configuration. We’ll enable it for the example but can disable later if no longer needed.
- ACS HTTPS Port: -1 or 443 - This is the port to use for HTTPS to the ACS (Assertion Consumer Service, in this case the UI). It is only needed if you need to use a non-standard https port
- SP Entity ID:
http://localhost:3000/service/sso/auth/keycloak(NOTE: this must match the Client ID you used for the Client in the KeyCloak setup - ACS URL:
http://localhost:3000/service/sso/auth/keycloak - Default Account:
keycloakusersfor this example, but can be any account name (existing or not) that you’d like the users to be members of. See Mappings for more information on how this - Default Role:
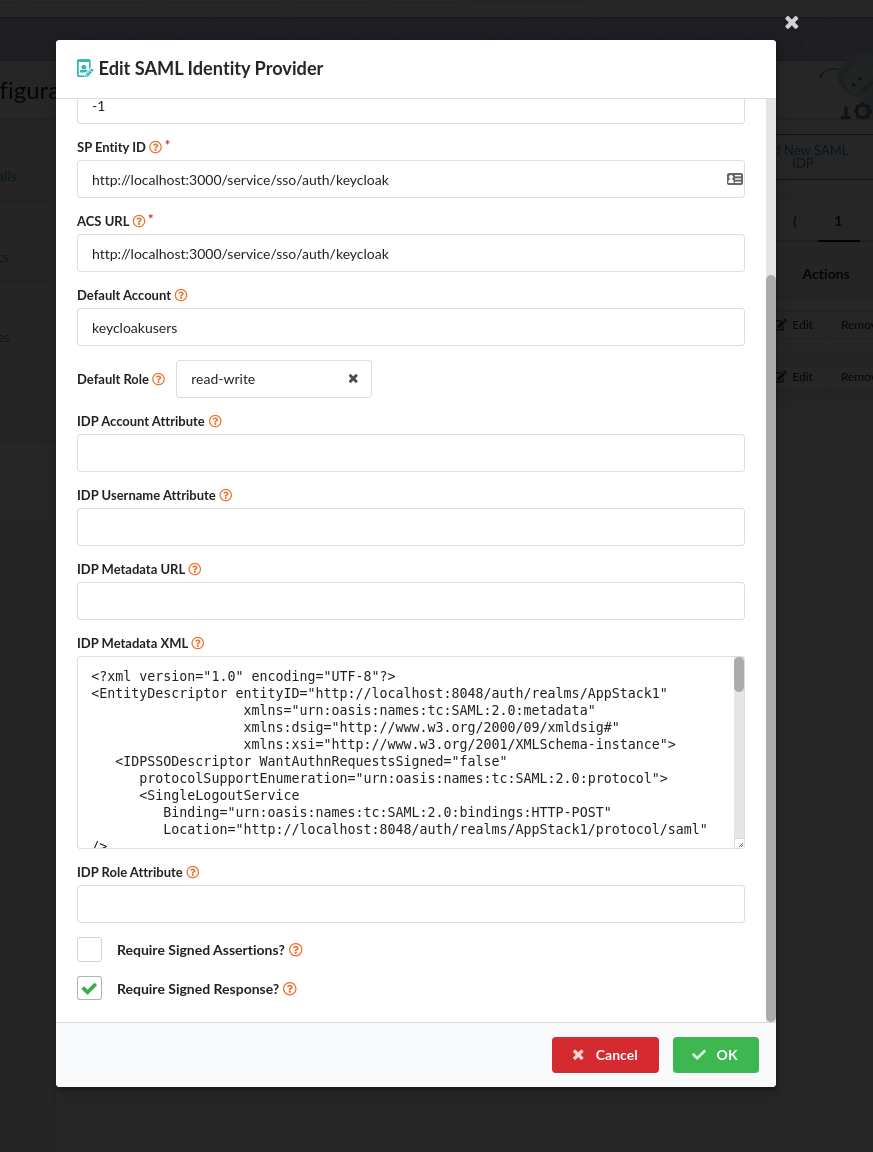
read-writefor this example so that the users have full access to the account to analyze images, setup policies, etc. - IDP Metadata XML: Paste the downloaded or copied XML from KeyCloak in step 4.3 above
- Require Signed Assertions - Select off
- Require Signed Response - Select on
- Save the configuration
You should now see a ‘keycloak’ option in the login screen for the Anchore Enterprise UI. This will redirect users to login to the KeyCloak instance for their username/password and will create a new user in Anchore in the keycloakusers account with read-write role.