Deploying Anchore Enterprise on OpenShift
This document will walkthrough the deployment of Anchore Enterprise on an OpenShift Kubernetes Distribution (OKD) 3.11 cluster and expose it on the public internet.
Note: While this document walks through deploying on OKD 3.11, it has been successfully deployed and tested on OpenShift 4.2.4 and 4.2.7.
Prerequisites
- A running OpenShift Kubernetes Distribution (OKD) 3.11 cluster. Read more about the installation requirements here.
- Note: If deploying to a running OpenShift 4.2.4+ cluster, read more about the installation requirements here.
- Helm client and server installed and configured with your cluster.
- AnchoreCTL installed on local host.
Anchore Helm Chart
Anchore maintains a Helm chart to simplify the software deployment process. An Anchore Enterprise installation of the chart will include the following:
- Anchore Enterprise Software
- PostgreSQL (13)
- Redis 4
To make the necessary configurations to the Helm chart, create a custom anchore_values.yaml file and reference it during deployment. There are many options for configuration with Anchore, this document is intended to cover the minimum required changes to successfully deploy Anchore Enterprise on OKD 3.11.
OpenShift Configurations
Create a new project
Create a new project called anchore-enterprise:
oc new-project anchore-enterprise
Create secrets
Two secrets are required for an Anchore Enterprise deployment.
Create a secret for the license file:
oc create secret generic anchore-enterprise-license --from-file=license.yaml=license.yaml
Create a secret for pulling the images:
oc create secret docker-registry anchore-enterprise-pullcreds --docker-server=docker.io --docker-username=<username> --docker-password=<password> --docker-email=<email>
Verify these secrets are in the correct namespace: anchore-enterprise
oc describe secret <secret-name>
Link ImagePullSecret
Link the above Docker registry secret to the default service account:
oc secrets link default anchore-enterprise-pullcreds --for=pull --namespace=anchore-enterprise
Verify this by running the following:
oc describe sa
Note: Validate your OpenShift SCC. Based on the security constraints of your environment, you may need to change SCC. oc adm policy add-scc-to-user anyuid -z default
Anchore Configurations
Create a custom anchore_values.yaml file for your Anchore Enterprise deployment:
# NOTE: This is not a production ready values file for an openshift deployment.
securityContext:
fsGroup: null
runAsGroup: null
runAsUser: null
feeds:
securityContext:
fsGroup: null
runAsGroup: null
runAsUser: null
feeds-db:
primary:
containerSecurityContext:
enabled: false
podSecurityContext:
enabled: false
postgresql:
primary:
containerSecurityContext:
enabled: false
podSecurityContext:
enabled: false
ui-redis:
master:
podSecurityContext:
enabled: false
containerSecurityContext:
enabled: false
Install software
Run the following command to install the software:
helm repo add anchore https://charts.anchore.io
helm install anchore -f values.yaml anchore/enterprise
It will take the system several minutes to bootstrap. You can checks on the status of the pods by running oc get pods:
$ oc get pods
NAME READY STATUS RESTARTS AGE
anchore-enterprise-analyzer-7f9c7c65c8-tp8cs 1/1 Running 0 13m
anchore-enterprise-api-754cdb48bc-x8kxt 3/3 Running 0 13m
anchore-enterprise-catalog-64d4b9bb8-x8vmb 1/1 Running 0 13m
anchore-enterprise-notifications-65bd45459f-q28h2 2/2 Running 0 13m
anchore-enterprise-policy-657fdfd7f6-gzkmh 1/1 Running 0 13m
anchore-enterprise-reports-596cb47894-q8g49 1/1 Running 0 13m
anchore-enterprise-simplequeue-98b95f985-5xqcv 1/1 Running 0 13m
anchore-enterprise-ui-6794bbd47-vxljt 1/1 Running 0 13m
anchore-feeds-77b8976c4c-rs8h2 1/1 Running 0 13m
anchore-feeds-db-0 1/1 Running 0 13m
anchore-postgresql-0 1/1 Running 0 13m
anchore-ui-redis-master-0 1/1 Running 0 13m
Create route objects
Create two route object in the OpenShift console to expose the UI and API services on the public internet:
Note: Route configuration is optional. It is used throughout this guide to expose the Anchore deployment on the public internet.
API Route
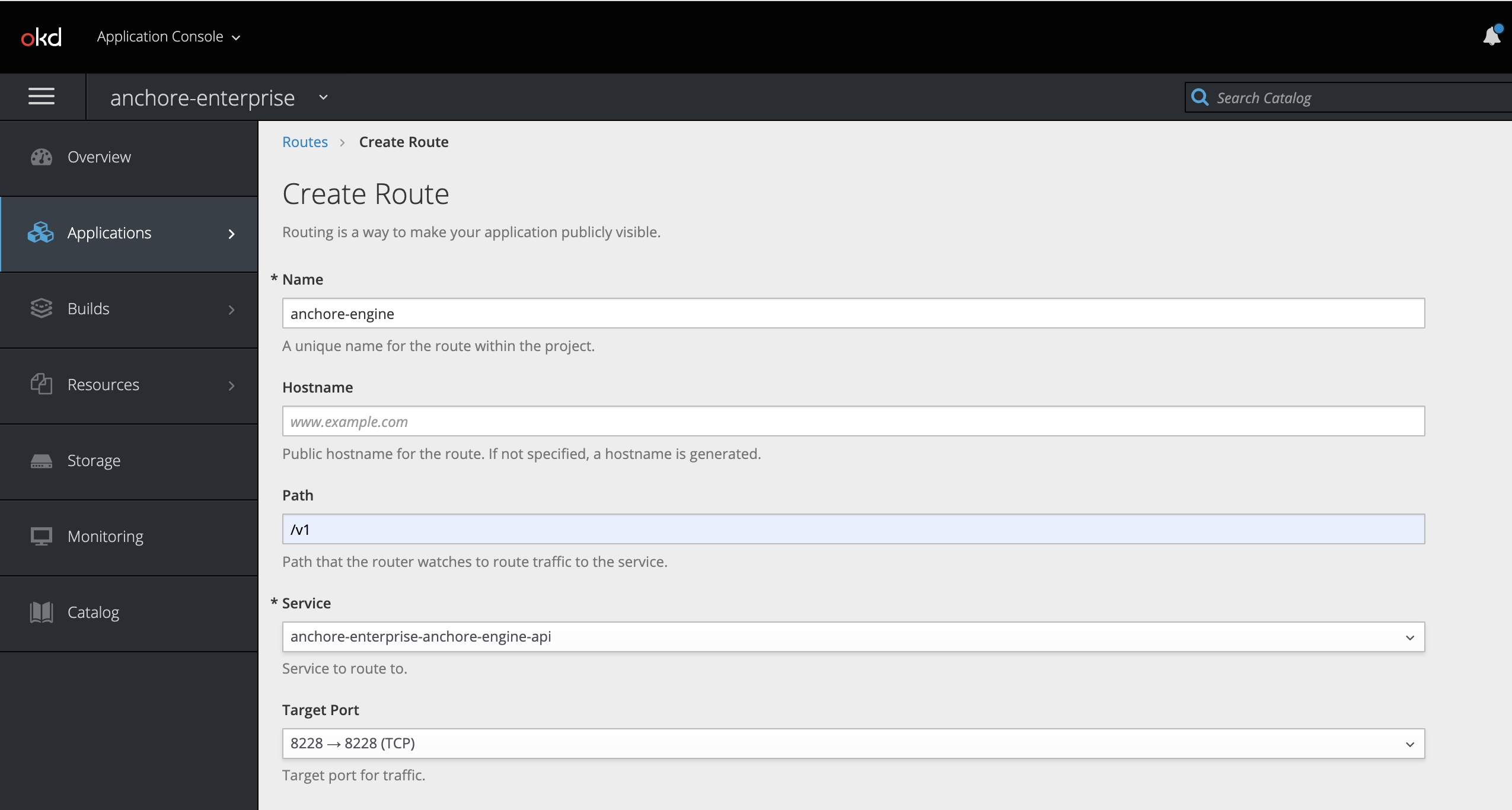
UI Route
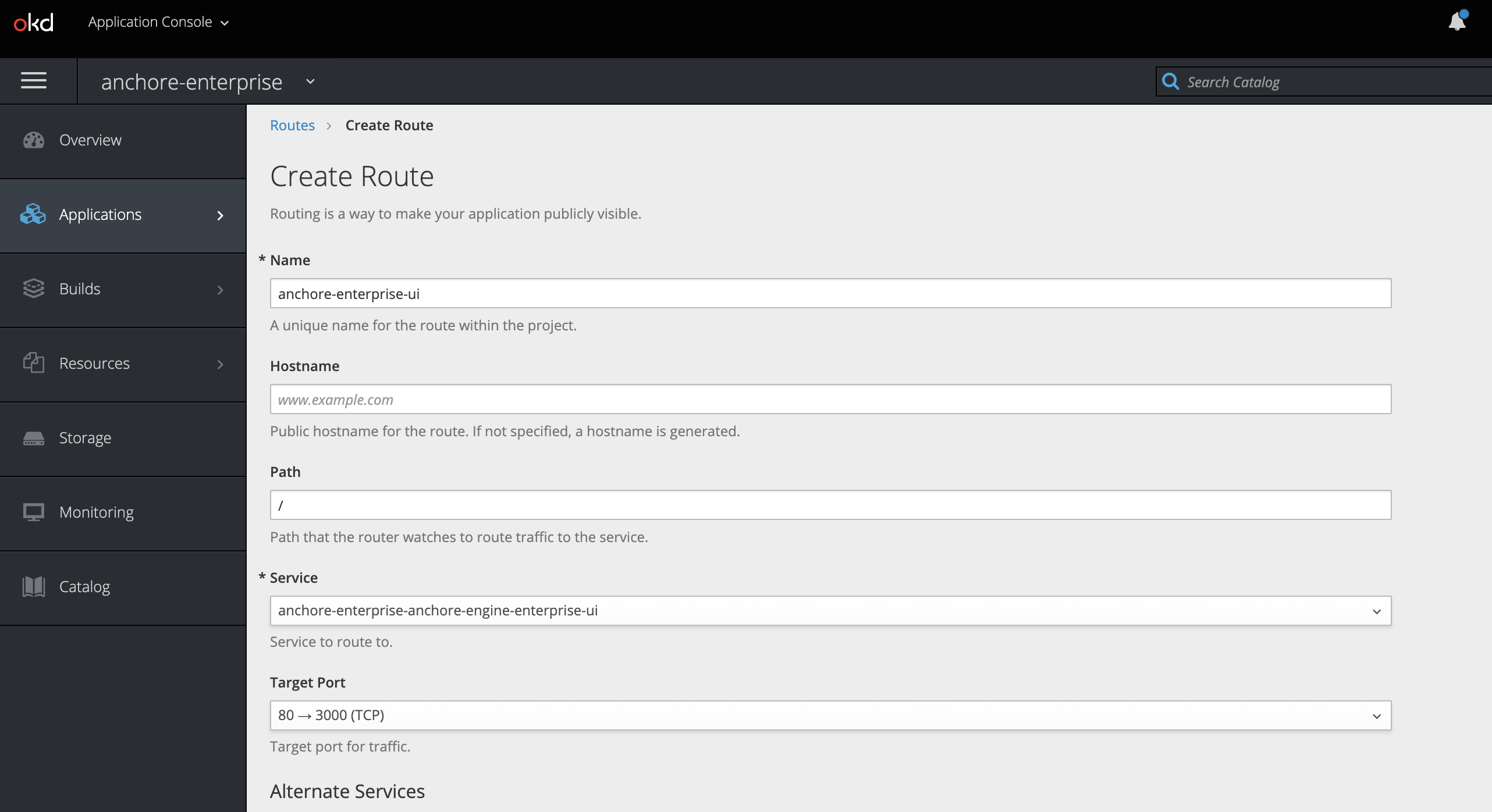
Routes
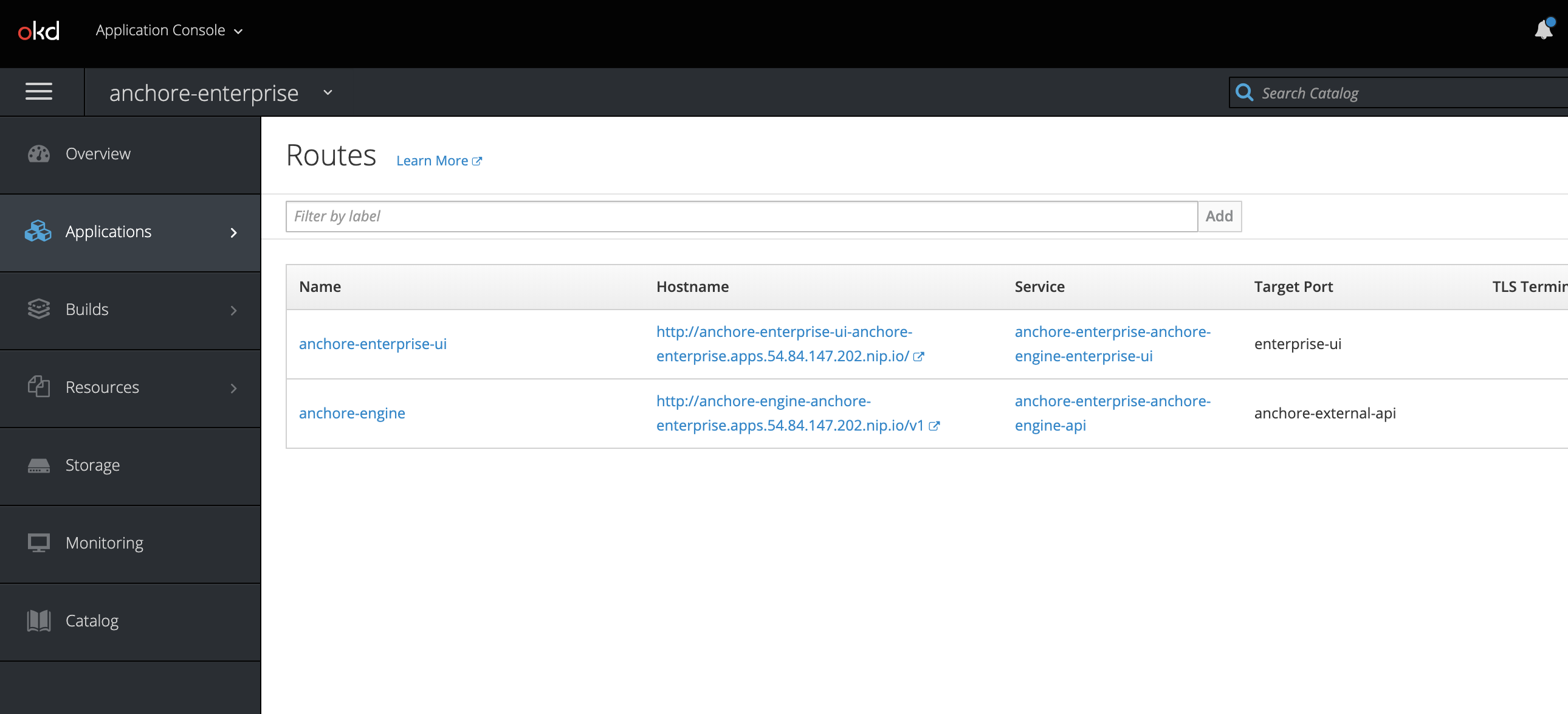
Verify by navigating to the anchore-enterprise-ui route hostname:
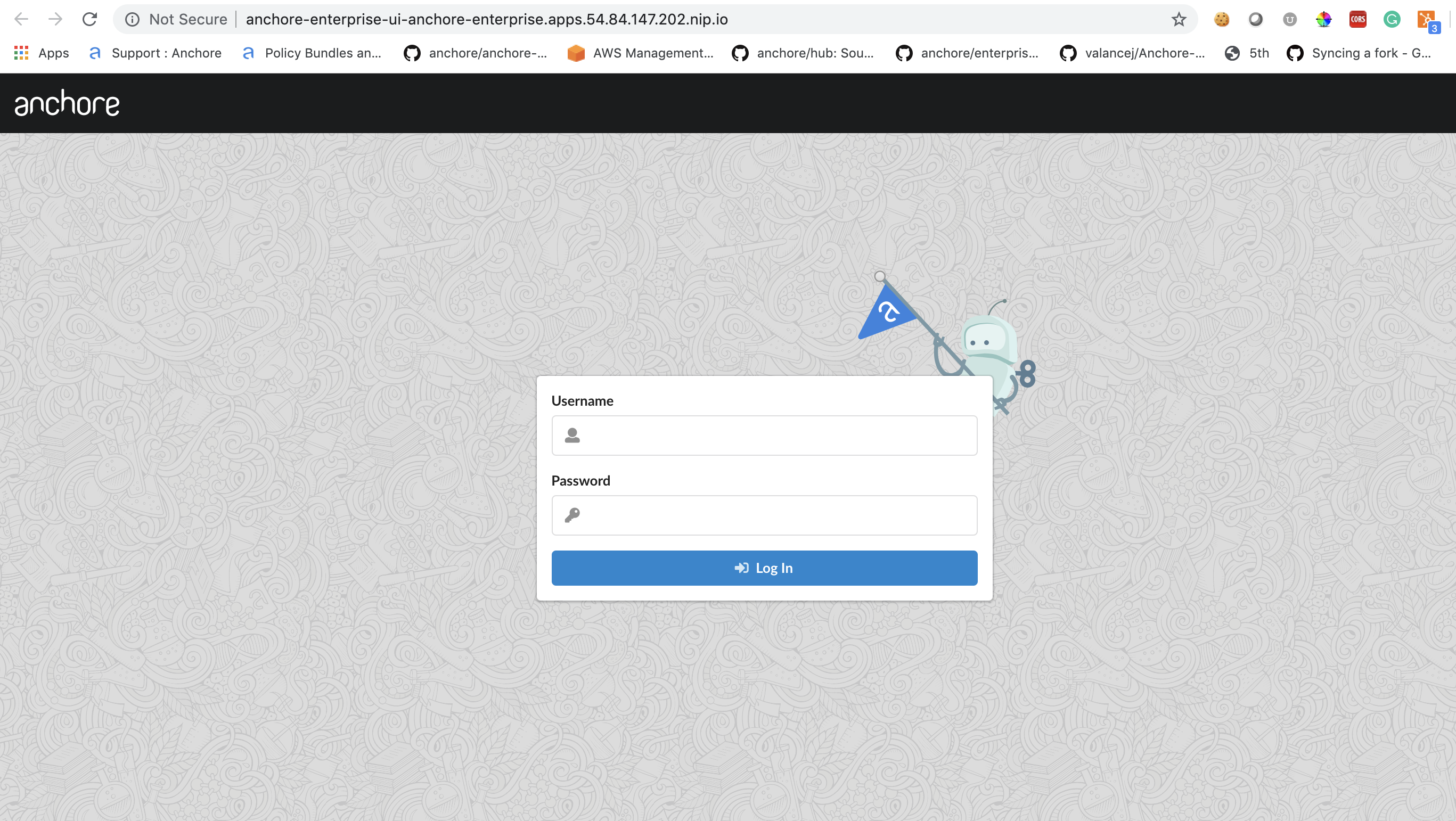
Anchore System
Verify API route hostname with AnchoreCTL:
Note: Read more on Deploying AnchoreCTL
# ANCHORECTL_URL=http://anchore-engine-anchore-enterprise.apps.54.84.147.202.nip.io ANCHORECTL_USERNAME=admin ANCHORECTL_PASSWORD=foobar anchorectl system status
...
...
Anchore Feeds
It can take some time to fetch all of the vulnerability feeds from the upstream data sources. Check on the status of feeds with AnchoreCTL:
# ANCHORECTL_URL=http://anchore-engine-anchore-enterprise.apps.54.84.147.202.nip.io ANCHORECTL_USERNAME=admin ANCHORECTL_PASSWORD=foobar anchorectl feed list
...
...
Note: It is not uncommon for the above command to return a: [] as the initial feed sync occurs.
Once the vulnerability feed sync is complete, Anchore can begin to return vulnerability results on analyzed images. Please continue to the Vulnerability Management section of our documentation for more information.
Last modified April 4, 2024