Anchore Enterprise Data Feeds
Anchore Data Service Overview
Anchore operates a hosted service called the Anchore Data Service that serves pre-built datasets to customer Enterprise deployments.
Anchore Data Service manages four datasets:
- Vulnerability Database (grypedb) - This dataset contains vulnerability data from the following sources:
- Alpine
- Amazon Linux
- Anchore Exclusions (CVEs that Anchore has excluded from the feed)
- Chain Guard
- Debian
- Github
- Mariner
- MSRC
- NVD (Including the Anchore Enhancements)
- Oracle
- RHEL
- SLES
- Ubuntu
- Wolfi
- ClamAV Malware Database - This dataset contains malware signatures that are used to detect malware in images.
- CISA Known Exploited Vulnerabilities (KEV) - This dataset contains vulnerability annotations that are used to provide additional context to vulnerabilities.
- Exploit Prediction Scoring System (EPSS) - This dataset contains exploit prediction scores for vulnerabilities.
These datasets are refreshed by pipelines that run every 6 hours.
Data Syncer Service Design
Anchore Enterprise includes a service, called the Data Syncer Service, that is responsible for syncing the datasets from the Anchore Data Service and making them available for use by the rest of Anchore Enterprise.
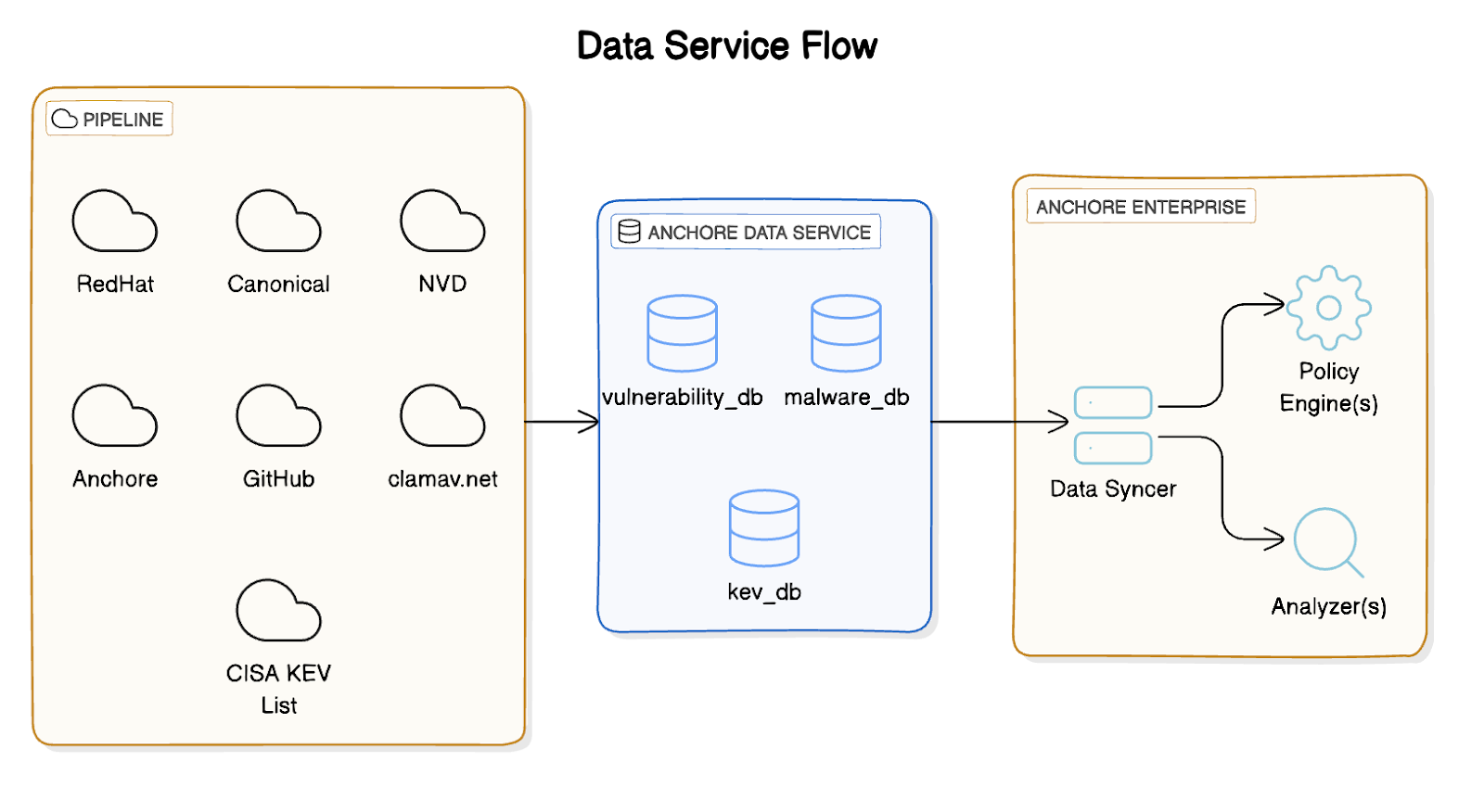
The following two FQDNs need to be allowlisted in your network to allow the Data Syncer Service to communicate with the Anchore Data Service:
https://data.anchore-enterprise.com
https://s3.us-west-2.amazonaws.com/enterprise-data-service.production.anchore.io
Authentication for this service is provided by your Anchore Enterprise license. No additional credentials are required.
To learn more, please review the Data Syncer Service Configuration doc.
Last modified December 9, 2024