Anchore SBOM - SBOM Management
Overview
Anchore SBOM is a set of capabilities in Anchore Enterprise that allow customers to gain comprehensive visibility into the software components present in both their internally developed and third-party supplied software to identify and mitigate security and compliance risks. It provides a centralized platform for viewing, managing, and analyzing Software Bill of Materials (SBOMs), including the capability to “Bring Your Own SBOMs” (BYOS) by importing SBOMs created outside of Anchore Enterprise and organizing them into groups, reflecting a logical organization structures for easier management, control, analysis, and reporting for enhanced collaboration across business and engineering functions. See below for a video walkthrough:
Why Are SBOMs Important?
Modern software is complex and often built by distributed teams on a foundation of open-source and third-party components. Staying secure and compliant requires continuous, end-to-end insight into the software stack. That means knowing exactly what’s in your applications at every stage of the DevOps lifecycle—from code to cloud. This is where SBOMs (Software Bills of Materials) come in. SBOMs are machine-readable inventories that capture the full composition of applications by listing every package and dependency they include.
How Anchore Enterprise Uses SBOMs
SBOMs are essential to Anchore Enterprise as they contain the package information that enables both the vulnerability scanning and policy enforcement capabilities to function.
A software bill of materials (SBOM) is a comprehensive inventory of the individual packages from source repositories and container images. One or more SBOMs can be grouped in higher-level applications to visualize related artifacts in applications by version. Applications are the top-level building block in a hierarchical view, and can represent any project your teams deliver.
Generating SBOMs for Anchore-Managed Assets
You can generate SBOMs using AnchoreCTL as part of a command line or CI/CD workflow, through pulling content from a registry, or by submitting an artifact to the Anchore API.
SBOMs can be managed using the command line, API, or GUI, where contents can be grouped, annotated, viewed, or searched. Artifact metadata, vulnerability information, and policy evaluations can also be viewed and managed through the same interfaces.
Security Engineers are often required to investigate security issues that stem from a source repository or from container images. The security team can use Anchore Enterprise to identify any open source security vulnerabilities or policy evaluation results which originate from a source code repository or image container. This helps them catch security issues earlier.
Managing External SBOMs
Importing external SBOMs enables users to go beyond standard container analysis by incorporating SBOMs generated outside of Anchore, whether from other SCA tools or vendor sources, in turn ensuring comprehensive visibility across all components of their applications.
Importing External SBOMs
External SBOMs can be imported in SPDX, CycloneDX, and Syft native formats. Imported SBOMs are validated for proper schemas and to ensure they meet the necessary data requirements for vulnerability scanning.
The SBOM formats supported for upload via the experimental SBOM Management features are:
- CycloneDX
- JSON: Versions 1.2 - 1.6
- XML: Versions 1.0 - 1.6
- SPDX
- JSON: Versions 2.2 - 2.3
- Tag-Value: Versions 2.1 - 2.3
- Initial SPDX 3.0 support for both JSON & Tag-Value, with the ability to upload and download these SBOMs, the content and vulnerability analysis of the SBOM contents will not be functional.
- Syft
Note that SBOMs produced via anchorectl distributed analysis do not meet the specifications of the above formats and are not supported for external SBOM imports.
To import an external SBOM, navigate to the Imported SBOMs view via the left navigation panel. In the top-right of the page, there is an Import SBOM button that will allow you to select the SBOM document you wish to import into Anchore Enterprise.
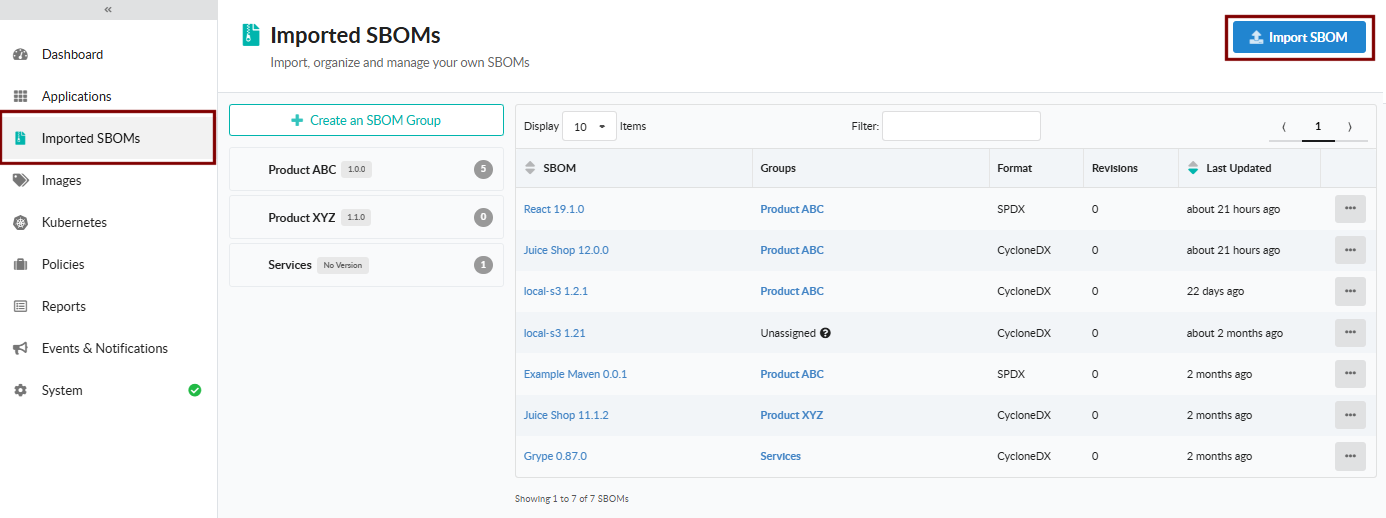
In the Import an SBOM dialog below, provide the following information:
- SBOM Name: A name for the SBOM document
- Version: A version for the SBOM document
- Groups: Optionally, select one or more SBOM groups with which to associate the imported SBOM
- Annotations: Optionally, add any annotations you would like to store with the imported SBOM; an example would be a Vendor for the application or module represented by the SBOM
- SBOM File: Select the SBOM document to import into Anchore Enterprise
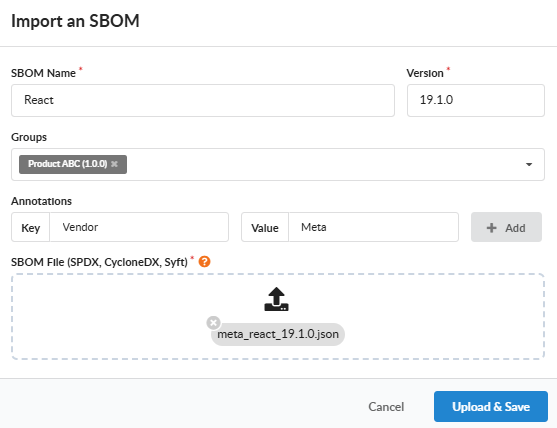
Document Insights
When importing an external SBOM, Anchore Enterprise will calculate a set of document insights which describe the properties of the given SBOM document. These document insights are used to indicate various quality metrics for the given SBOM, and result in an overall SBOM Quality score.
Note that support for xml and tag-value formats is achieved by converting the stored document to Syft json before inspection, and therefore the document insights will be calculated based on the converted version.
The metrics currently included in the document insights are:
- Valid Format
- True if the given document can be identified as a valid SBOM of one of these formats:
- CycloneDX
- SPDX
- Syft
- True if the given document can be identified as a valid SBOM of one of these formats:
- Valid Schema
- True if the filetype can be identified as one of:
- json
- xml
- spdx (tag-value)
- True if the filetype can be identified as one of:
- Supported Format:
- True if the given document format is within the set of formats that Anchore Enterprise can inspect for further insights. This set is currently:
- CycloneDX
- SPDX
- Syft
- True if the given document format is within the set of formats that Anchore Enterprise can inspect for further insights. This set is currently:
- Supported Schema:
- True if the given document filetype is within the set of filetypes that Anchore Enterprise can inspect for further insights. This set is currently:
- json
- xml
- spdx (tag-value)
- True if the given document filetype is within the set of filetypes that Anchore Enterprise can inspect for further insights. This set is currently:
- Artifacts Documented:
- True if the given document contains a set of artifacts or packages.
- CycloneDX
- True if the document contains a
componentslist of non-zero length.
- True if the document contains a
- SPDX
- True if the document contains a
packageslist of non-zero length.
- True if the document contains a
- Syft
- True if the document contains an
artifactslist of non-zero length.
- True if the document contains an
- CycloneDX
- True if the given document contains a set of artifacts or packages.
- Dependencies Documented:
- True if the given document contains a set of dependencies.
- CycloneDX
- True if the document contains a
dependencieslist of non-zero length.
- True if the document contains a
- SPDX
- True if the document contains a
relationshipslist of non-zero length.
- True if the document contains a
- Syft
- True if the document contains an
artifactRelationshipslist of non-zero length.
- True if the document contains an
- CycloneDX
- True if the given document contains a set of dependencies.
- Author Documented:
- True if the given document contains metadata on the author of the document.
- CycloneDX
- True if the
metadataobject of the given document contains either a non-nullmanufacturervalue or anauthorslist of non-zero length.
- True if the
- SPDX
- True if the
creationInfoobject of the given document contains acreatorslist of non-zero length.
- True if the
- Syft
- Not present in the Syft specification.
- CycloneDX
- True if the given document contains metadata on the author of the document.
- Supplier Documented:
- True if the given document contains metadata on the supplier of the artifacts.
- CycloneDX
- True if the
metadataobject of the given document contains a non-nullsuppliervalue.
- True if the
- SPDX
- True if entries in the
packageslist of the given document contain asuppliervalue that is not empty and is not equal toNOASSERTION.
- True if entries in the
- Syft
- Not present in the Syft specification.
- CycloneDX
- True if the given document contains metadata on the supplier of the artifacts.
- Document Timestamp:
- True if the given document contains metadata on the creation date-time of the document.
- CycloneDX
- True if the
metadataobject of the given document contains a non-nulltimestampvalue.
- True if the
- SPDX
- True if the
creationInfoobject of the given document contains a non-nullcreatedvalue.
- True if the
- Syft
- Not present in the Syft specification.
- CycloneDX
- True if the given document contains metadata on the creation date-time of the document.
- SBOM Quality:
- The percentage of the above metrics that are True for the given document.
Organizing Imported SBOMs
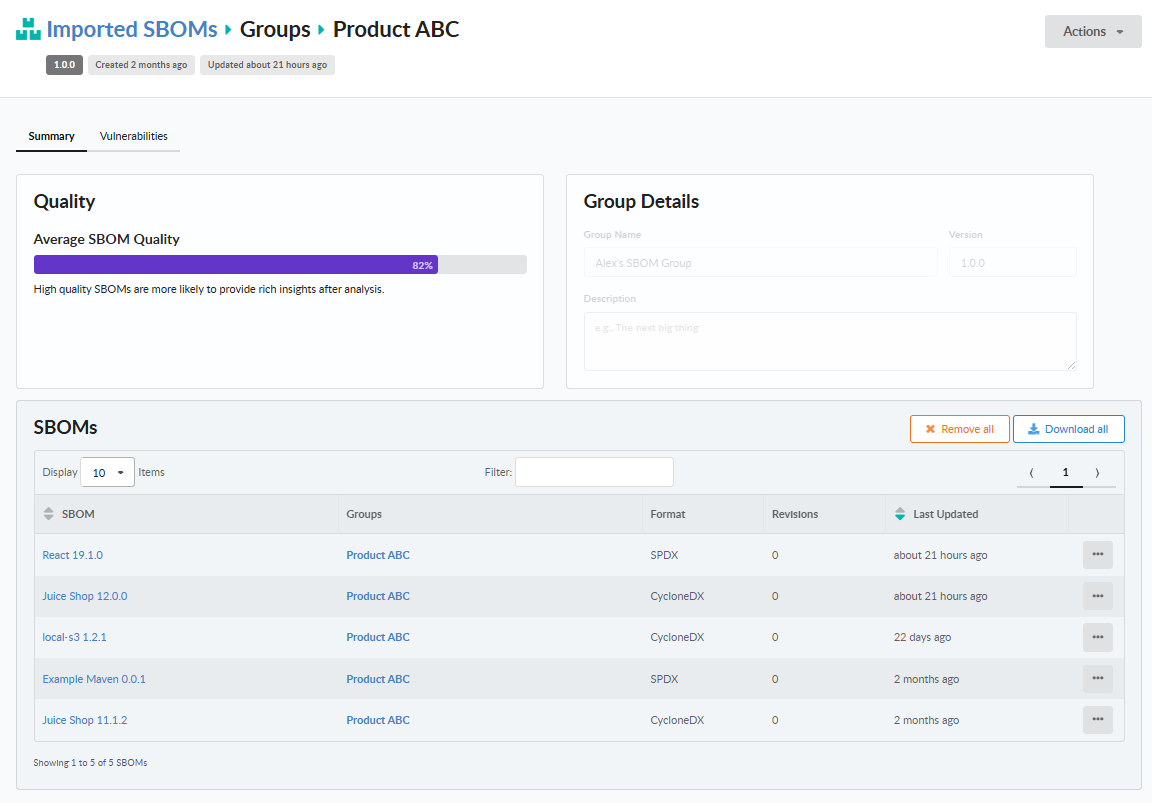
Imported SBOMs can be placed into groups to reflect logical organization structures. This can be done as part of an SBOM import, or later once an SBOM has already been imported into Anchore Enterprise.
The SBOM Group Summary view shows the list of associated imported SBOMs along with their key attributes. The group SBOM Quality score shows the average SBOM Quality scores across all of the constituent SBOMs.
Viewing SBOM Contents
To view the contents for an imported SBOM, click on the Contents tab as shown below:
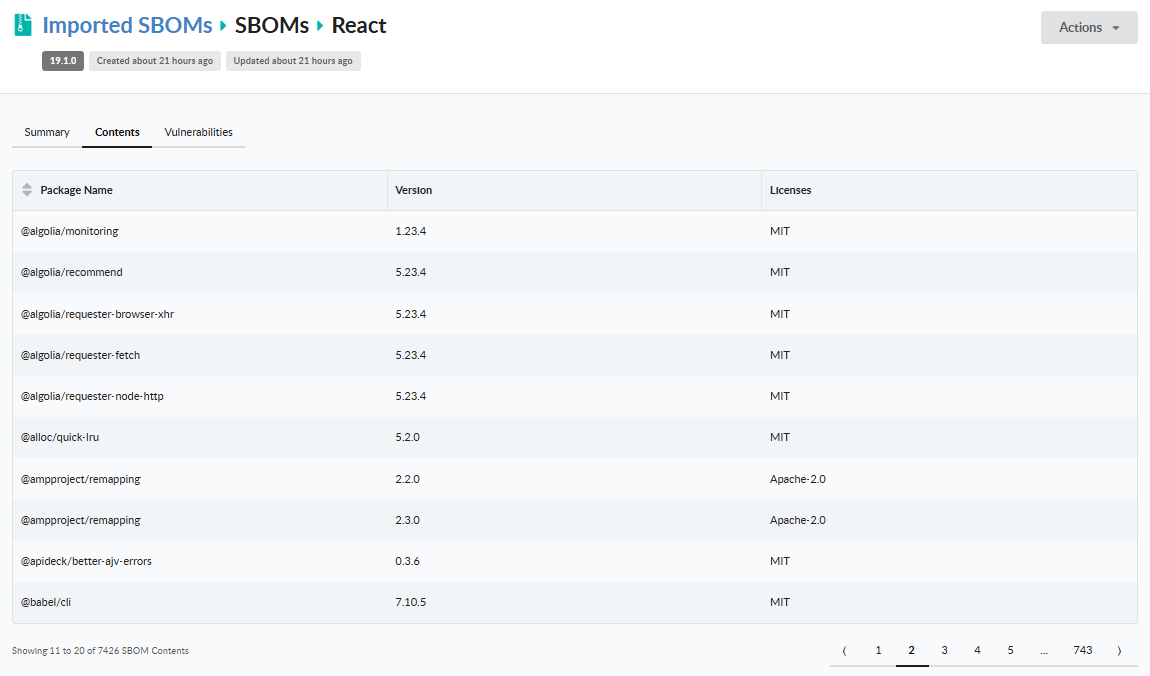
A list of packages, versions, and associated licenses are displayed representing the contents of the current SBOM.
Vulnerability Scanning for Imported SBOMs
Once uploaded, imported SBOMs are placed into a queue to be scanned for vulnerabilities.
Once scanned, vulnerability results can be viewed for a particular imported SBOM or SBOM Group by clicking on the Vulnerabilities tab as shown below:
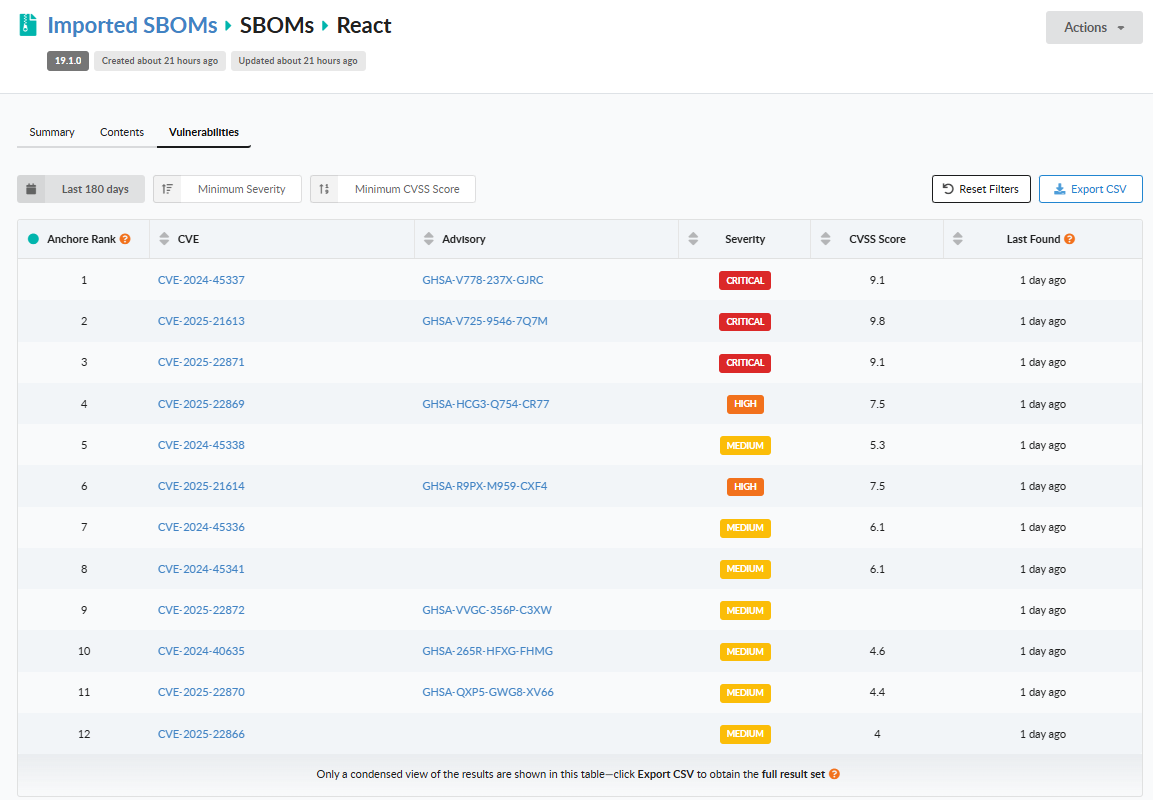
The list of vulnerabilities can be filtered using the following criteria:
- Vulnerability Age: select the number of days since the last time a particular vulnerability has been reported
- Minimum Severity: select the desired minimum CVSS severity
- Minimum CVSS Score: select the desired minimum CVSS score
The Reset Filters button can be used to revert all filters back to their default values.
The Anchore Rank column provides a sequence value for each vulnerability that can be used to prioritize vulnerability review and remediation. This sequence value is based on the new Anchore Score, which is a composite security index comprised of the CVSS Score and Severity, EPSS percentage, and CISA KEV status. The higer the value, the more significant the vulnerability and the higher the priority to address it.
The Export CSV button in the top-right can be used to export all data for the filtered set of vulnerabilities into a CSV file.
Please note that while the UI only displays the key vulnerability fields and limits the number of displayed vulnerabilities to 100, the CSV data file will include all data fields for the complete set of vulnerabilities matching the filter criteria. Furthermore, the CSV data file will include a record for each vulnerability instance per the affected package and the SBOM containing the affected package.
Performance Considerations
Though no explicit limits are enforced, 10,000 SBOMs and 1,000 Groups have been used as the target for optimal performance in this release.
The SBOM scanning queue has been optimized to facilitate a full rescan of your imported SBOM inventory every 6 hours. SBOMs are scanned using a First In, First Out (FIFO) queue, meaning that the oldest SBOMs in the queue are scanned first.
For more information on the performance and configuration of the scanning queue, see Imported SBOM Scanning.
SBOM Management API (Experimental)
Appropriate user permissions are required to access these API endpoints.