If you’ve successfully verified that all Anchore Enterprise services are up, but are still running into issues operating Anchore, a good place check is the event log.
The event log subsystem provides users with a mechanism to inspect asynchronous events occurring across various Anchore Enterprise services. Anchore events include periodically-triggered activities such as vulnerability data feed sync in the policy_engine service, image analysis failures originating from the analyzer service, and other informational or system fault events. The catalog service may also generate events for any repositories or image tags that are being watched when Anchore Enterprise encounters connectivity, authentication, authorization, or other errors in the process of checking for updates.
The event log is aimed at troubleshooting most common failure scenarios, especially those that happen during asynchronous operations, and to pinpoint the reasons for failures that can be used subsequently to help with corrective actions. Events can be cleared from Anchore Enterprise in bulk or individually.
Viewing Events
The recent events can be viewed inside the Anchore UI on the ‘Events & Notifications’ tab:
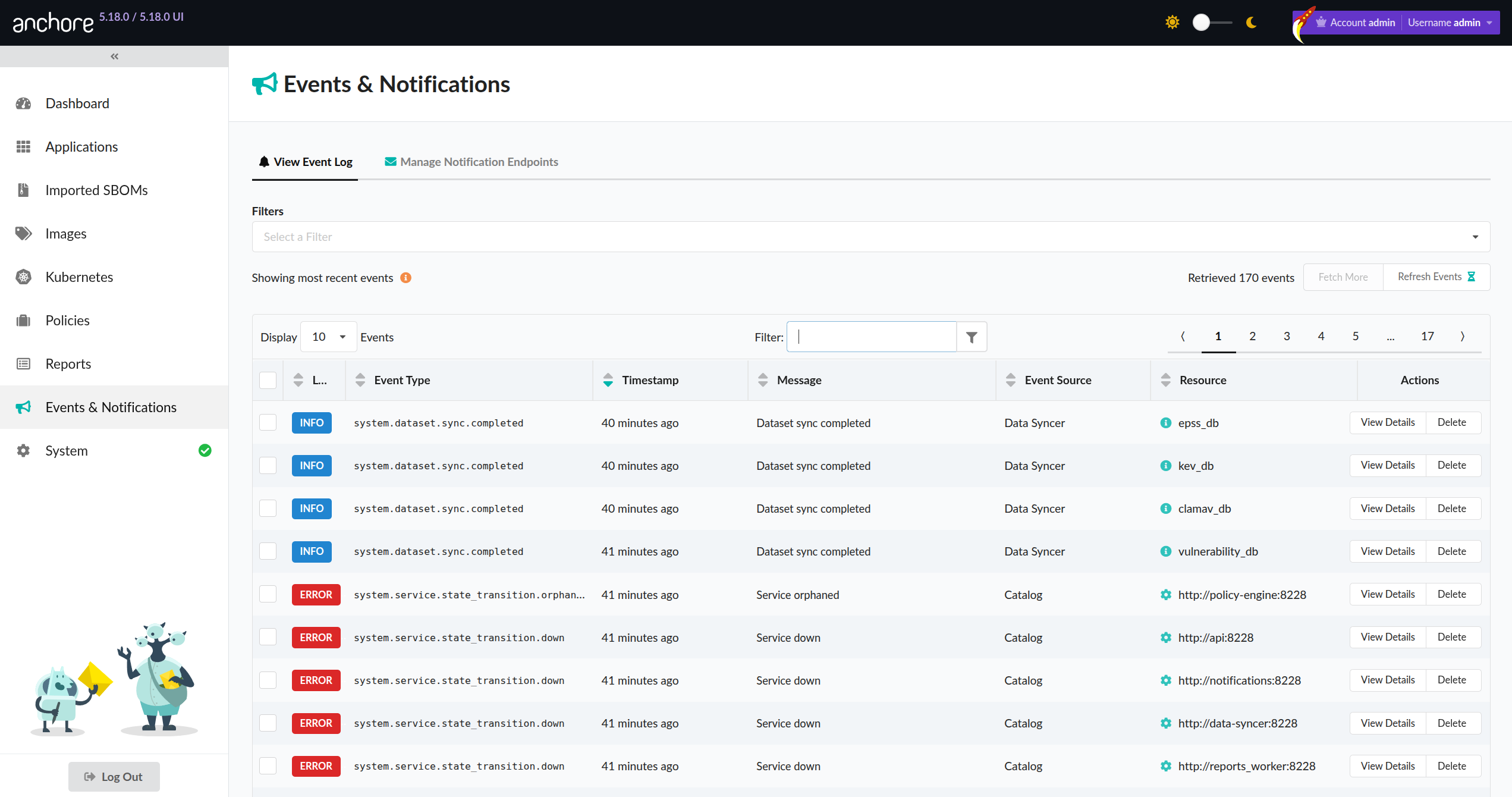
If using AnchoreCTL, running the following command will give a list of recent Anchore events: anchorectl event list
Viewing list of recent Anchore events
anchorectl event list
✔ List events
┌──────────────────────────────────┬──────────────────────────────────────────────┬───────┬───────────────────────────────────────────────────────┬─────────────────┬────────────────┬────────────────────┬─────────────────────────────┐
│ UUID │ EVENT TYPE │ LEVEL │ RESOURCE ID │ RESOURCE TYPE │ SOURCE SERVICE │ SOURCE HOST │ TIMESTAMP │
├──────────────────────────────────┼──────────────────────────────────────────────┼───────┼───────────────────────────────────────────────────────┼─────────────────┼────────────────┼────────────────────┼─────────────────────────────┤
│ 329ff24aa77549458e2656f1a6f4c98f │ system.image_analysis.registry_lookup_failed │ error │ dockerr.io/alpine:3.4 │ image_reference │ catalog │ anchore-quickstart │ 2022-08-24T22:08:29.026352Z │
│ 4010f105cf264be6839c7e8ca1a0c46e │ system.image_analysis.registry_lookup_failed │ error │ dockerr.io/alpine:latest │ image_reference │ catalog │ anchore-quickstart │ 2022-08-24T22:08:28.991101Z │
│ 6924eb83313746ff8b842a88654e3ac1 │ system.image_analysis.registry_lookup_failed │ error │ dockerr.io/alpine:3.12 │ image_reference │ catalog │ anchore-quickstart │ 2022-08-24T22:08:28.956321Z │
│ efdcf727647c458f85cb6464926e474d │ system.image_analysis.registry_lookup_failed │ error │ dockerr.io/nginx:latest │ image_reference │ catalog │ anchore-quickstart │ 2022-08-24T22:08:28.920222Z │
...
│ 1eb04509b2bc44208cdc7678eaf76fef │ user.image.analysis.completed │ info │ docker.io/ubuntu:latest │ image_tag │ analyzer │ anchore-quickstart │ 2022-08-24T22:06:13.736004Z │
│ 6f735f8db7e84ce19b221d3b024318af │ user.image.analysis.processing │ info │ docker.io/ubuntu:latest │ image_tag │ analyzer │ anchore-quickstart │ 2022-08-24T22:06:13.128912Z │
│ 480eb191f87440b48c9f8cfa6529badf │ user.image_tag.added │ info │ docker.io/ubuntu:latest │ image_tag │ catalog │ anchore-quickstart │ 2022-08-24T22:06:08.307039Z │
...
└──────────────────────────────────┴──────────────────────────────────────────────┴───────┴───────────────────────────────────────────────────────┴─────────────────┴────────────────┴────────────────────┴─────────────────────────────┘
Details about a specific event
If you would like more information about a specific event, you can run the following command: anchorectl event get <event-id>
Details about a specific Anchore event
anchorectl event get 1eb04509b2bc44208cdc7678eaf76fef
✔ Fetched event
UUID: 1eb04509b2bc44208cdc7678eaf76fef
Event:
Event Type: user.image.analysis.completed
Level: info
Message: Image analysis available
Resource:
Resource ID: docker.io/ubuntu:latest
Resource Type: image_tag
User Id: admin
Source:
Source Service: analyzer
Base Url: http://analyzer:8228
Source Host: anchore-quickstart
Request Id:
Timestamp: 2022-08-24T22:06:13.736004Z
Category:
Details:
Created At: 2022-08-24T22:06:13.832881Z
Note: Depending on the output from the detailed events, looking into the logs for a particular servicename (example: policy_engine) is the next troubleshooting step.